Jeremy Moskowitz founded PolicyPak Software after working with hundreds of customers with the same problem they couldn’t manage their applications, browsers and operating systems using the technology they already utilized.

AppLocker Pros, Cons, and Alternatives
AppLocker is an application control feature found in enterprise editions of Windows. The tool enables you to manage which applications and files users can run. Windows AppLocker aims to limit software access and related data from specific users and business groups. The results of which is heightened security reduced administrative overhead and fewer helpdesk calls.
Why AppLocker, why now?
It’s a malware world out there. New malware strains pop up throughout the world today like weeds on a warm spring day. According to Infosecurity Group, researchers detected over 360,000 new malicious files in 2017. That equates to about four new malware samples every second. Albeit a considerable quantity, the number of new malicious exploits isn’t surprising. The bad guys use automation to generate and distribute malware variants. As a result, the antimalware community struggles to keep up.
Microsoft AppLocker provides out-of-the-box application whitelisting (AWL) capabilities that prevents users from running possibly dangerous applications. Application Whitelisting (AWL) is a Defence in Depth strategy that specifies the authorized applications for use within a computer network. There are multiple ways that users can intentionally and unintentionally download malicious software.
- User inadvertently clicked an arbitrary EXE file deposited onto their computer
- A disgruntled user downloaded a trojan horse knowingly
- Maybe someone in the organization planted a file
Ultimately, when you use Windows AppLocker to whitelist applications, you are specifying the exact applications and .exe files that users may open. Malware stays at bay because you are limiting an end user’s potential to cause harm. The beauty of AppLocker is that if an extension isn’t on the whitelist, it doesn’t get opened. Simplicity at its finest, at least in theory. In reality, the list of authorized applications within most enterprises continually changes. Meaning, whitelists require constant maintenance and modifications. This flaw is the inherent weakness of most whitelist solutions.
AppLocker Pros
AppLocker has several significant benefits. First, Microsoft includes AppLocker with the enterprise edition of Windows Server. Meaning, it doesn’t cost extra. Second, AppLocker comes as an integrated part of Group Policy. Most Windows administrators are already familiar with Group Policy, which makes AppLocker user experience seamless and natural. Third, you can import any AppLocker policy into Intune as an XML file. Thus, you possess nearly the same control of applications for MDM-enrolled devices as you would for on-premises, domain-joined devices. Finally, AppLocker automatically whitelists internal Windows applications, thereby saving you time and removing complexity.
AppLocker Cons
Nevertheless, AppLocker has numerous drawbacks that lower productivity and increase risk. For starters, AppLocker, like most whitelisting solutions, requires you to update and tweak your index of authorized applications continuously. In truth, the process of maintaining a company-wide whitelist is long, arduous and requires a significant amount of time and effort. Furthermore, anyone with admin rights to their local device can subvert AppLocker Policies. As a result, you may expose your environment to malware despite your best efforts to lock down applications.
Above all, AppLocker has one glaring flaw. See if you can figure it out. Below are the Windows operating systems that AppLocker supports.
- Ultimate and Enterprise editions of Windows 7
- Enterprise edition of Windows 8
- Education and Enterprise editions of Windows 10
- Server 2008 R2, Server 2012, Server 2012 R2, Server 2016 and Server 2019
If you noticed that Windows Professional editions are missing from this list, you guessed correctly. When applied with Group Policy, AppLocker doesn’t play nice with Windows 10 Professional. Meaning, you’ll have to look elsewhere to lock down applications on domain-joined machines.
AppLocker Alternatives
Before committing to AppLocker, you should perform a due diligence analysis of alternative solutions. By looking elsewhere, you’ll have a better understanding of the competitive landscape and can make a more informed decision.
PolicyPak is a Windows endpoint management and security solution that provides more control over user and computer settings. The solution includes Least Privilege Manager, which provides locks down all permissions except the ones that users require to conduct critical business functions. PolicyPak Least Privilege Manager enables standard users to do their jobs without possessing local admin rights. Moreover, PolicyPak shields Windows computers from malware without sacrificing productivity. Opposed to AppLocker, PolicyPak is designed to accelerate the whitelisting process. In other words, Windows Administrators have much more time to work on critical infrastructure tasks. Unlike AppLocker, PolicyPak works with the Windows Professional edition of Windows 7 and later. Whitelisting benefits aren’t limited to just a few select operating systems.
AppLocker vs. PolicyPak
PolicyPak Least Privilege Manager differs from AppLocker in several ways. First, PolicyPak elevates privileges for a standard user when they need something. For example, a graphic designer may need to install an application for mocking up a new user interface. In this case, PolicyPak Least Privilege Manager would permit them to perform the installation. As another example, consider a remote employee who needs to add a printer. PolicyPak Least Privilege would allow them to bypass UAC prompts or grant them access to designated Control Panel applets. Second, PolicyPak includes SecureRun™, which only lets users run applications if they are “properly installed or sanctioned by the administrator.” Like AppLocker, PolicyPak integrates with Group Policy and allows for the creation, assignment, and deployment of policies. See an example of the policy creation process below.
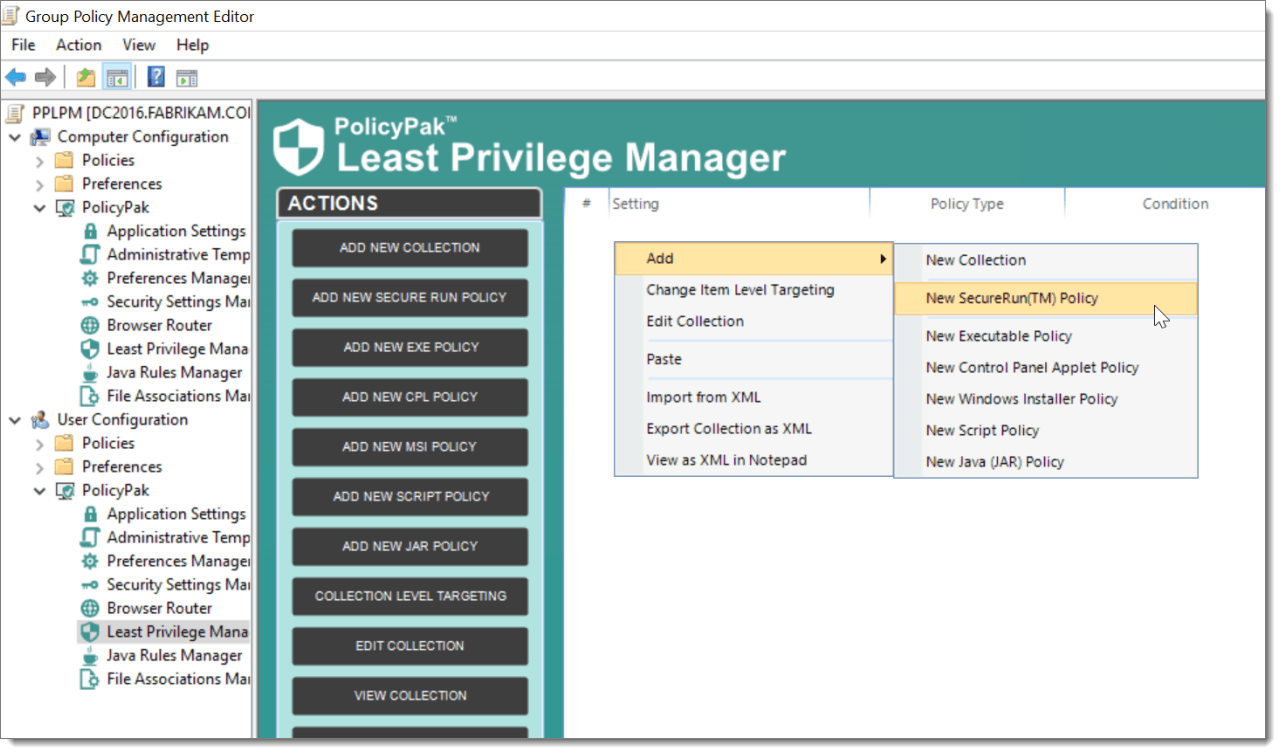
The premise behind SecureRun™ is straightforward. Someone owns every application, file executable, MSI, script or Java JAR file. When users download a file from the internet or copy it from a shared drive, they own it. See an example below:
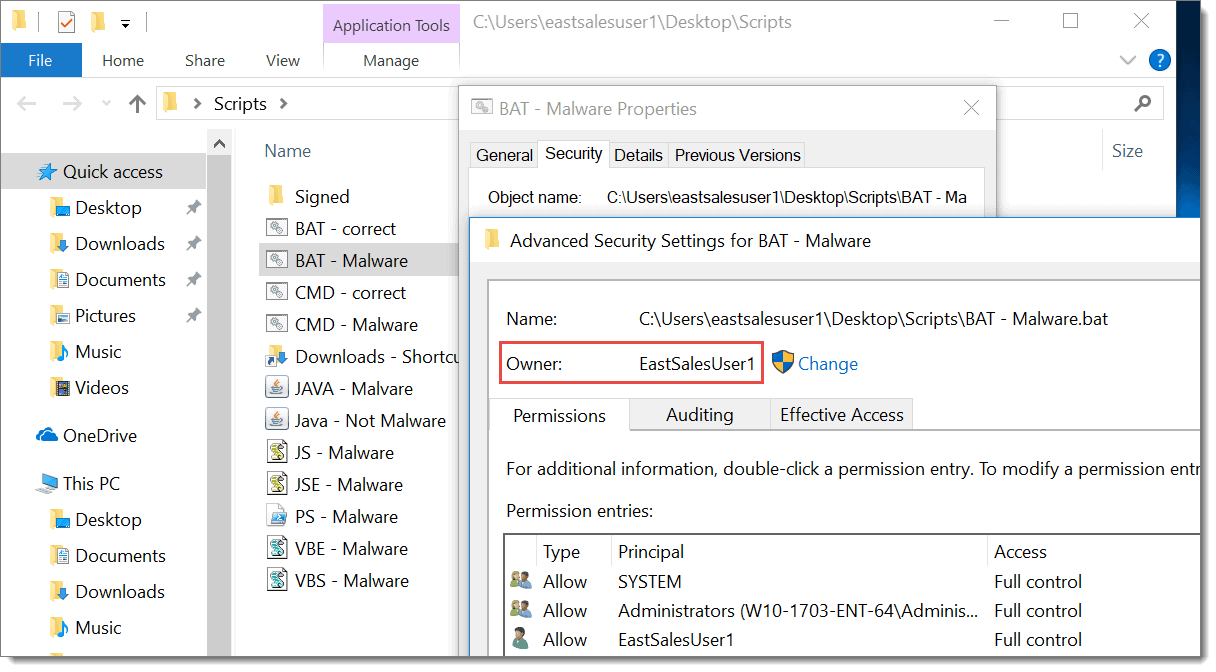
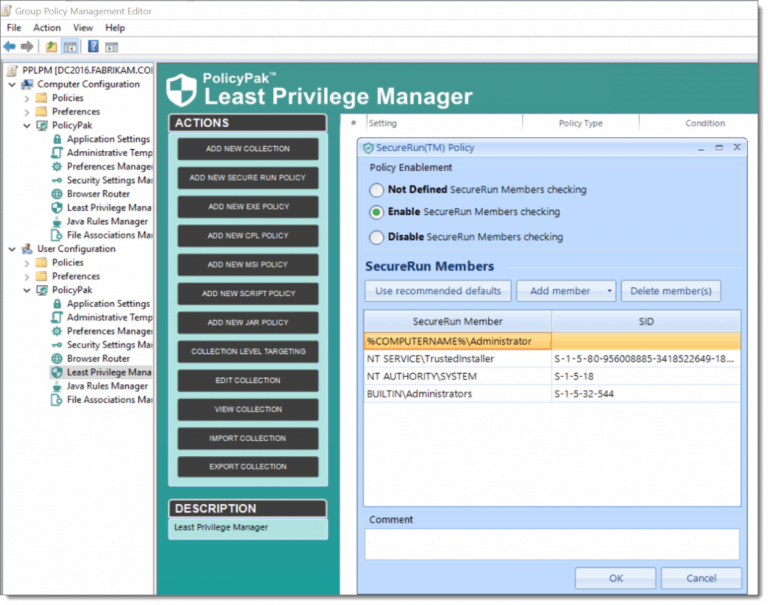
SecureRun™ looks to see who owns one of these files when a user wants to open it. It then compares this with an ownership list that you define. See an example of a default list here:
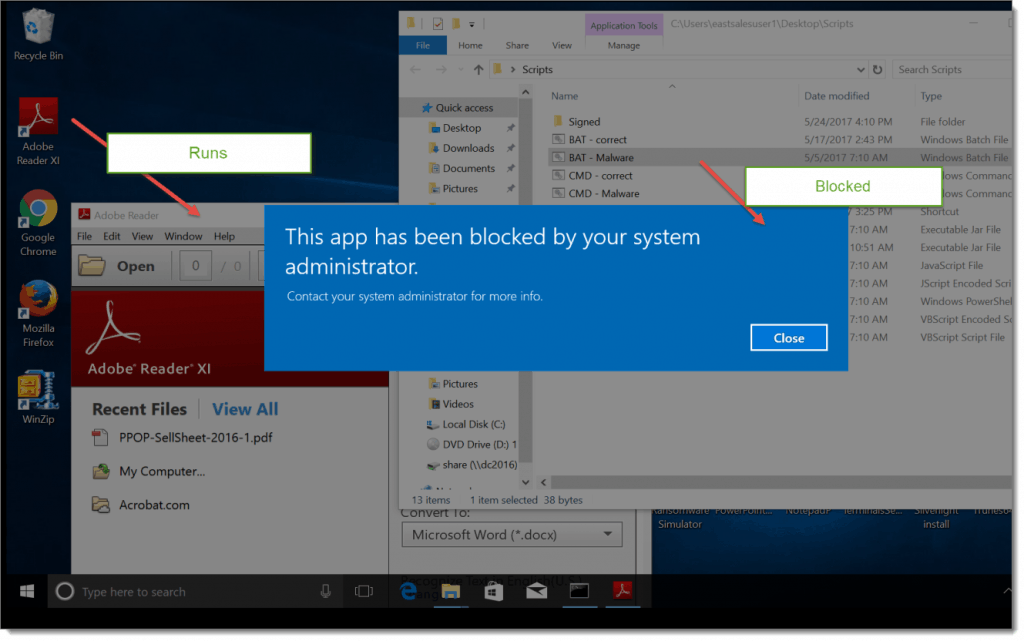
So, an application that was installed correctly by an administrator or technical support specialist is run perfectly well as always. An application downloaded and then executed by a Standard User gets the deny message seen below.
One of the most elegant and convenient aspects of PolicyPak Least Privilege Manager is that you don’t have to update your list of approved applications regularly. Opposed to AppLocker, PolicyPak isn’t dependent on applications themselves. Instead, it leverages the Administrator role which grants access to applications. In summary, applications may come and go, but the administrators’ group stays consistent forever. You can see a short video demonstrating the SecureRun™ process and how it secures the desktop here.
AppLocker Final Thoughts and Next Steps
Unlike Applocker, PolicyPak Least Privilege Manager does more than just whitelist applications. It works in any situation that requires standard users to move past UAC prompts. Furthermore, it elevates the situation and not the person.
Whether it’s an application, a Control Panel applet or a distributed PowerShell script, standard users can execute and elevate as needed. By delegating these privileges, you give standard users the ability to do their job without them impeding on yours. In other words, you can put a stop them continually calling and opening up help desk tickets when they encounter a UAC prompt. The combination of elevating rights, along with whitelisting via PolicyPak SecureRun™ is what separates PolicyPak Least Privilege Manager from AppLocker and other standard AWL solutions.


