Jeremy Moskowitz founded PolicyPak Software after working with hundreds of customers with the same problem they couldn’t manage their applications, browsers and operating systems using the technology they already utilized.

Using Credential Guard with Group Policy to stop Credential Theft
What is the anatomy of a compromise? In the cases of Target, Home Depot, and many more companies, stolen credentials lead to the compromise of millions of credit card numbers.
Credentials are typically stolen in a few ways:
- Phishing attacks that trick end users into giving bad actors their information.
- Brute force attacks or randomly guessing combinations.
- Running compromised software that extracts credentials from a computer system.
How can you help protect your environment from these issues? There are three “low tech ways” to get started:
- User Training and Acceptable use policies- Annual training and acceptable use training help end-users learn to spot and avoid threats.
- Requiring long passwords or passphrases. Long passwords reduce the effectiveness of brute force attacks
- Regular updates and security patching. Keeping computer systems up to date can help protect against known threats.
But what happens when these low tech methods are not effective enough? Humans are prone to making mistakes, passwords can still be guessed, software can have unknown vulnerabilities, and sometimes we need some technical backup against the bad guys.
To help Microsoft has also introduced a technology in Windows 10 called Credential Guard.
Credential Guard is designed to help protect credentials from being stolen by malicious programs like the Trojan that stole the credentials in the Target compromise.
What happens when computers do not have their credentials protected? As we hinted above, systems that don’t have their credentials protected, leaving them vulnerable to compromise. All it takes is a good Zero-Day exploit or tricking a human into clicking on a maliciously formed link in an email. Just enough to give an attacker a foothold in the environment.
Without Credential Guard enabled, malicious programs and actors are able to dump credentials from the Local Security Authority. An attacker might get a user to click on a compromised link or run malicious software which will then allow the bad actor to extract the users credentials. A proof-of-concept example of that can be seen here.
Protecting your credentials with Credential Guard
Credential Guard is built into Windows 10 Enterprise and Windows Server 2016. To do its work, it uses virtualization-based security to isolate credentials.
Credentials can include:
- NTLM password hashes
- Kerberos tickets and
- Domain application passwords
These are isolated from advanced malicious applications running, even programs running with administrative access. These credentials are stored in a VM which is tied to the TPM chip on the physical machine which makes cracking the credentials not possible (as of this writing.)
Credential Guard Requirements
Computers that meet certain hardware and software requirements can use Credential Guard to help add an extra layer of security. Credential Guard easily be deployed in an environment providing that the environment meets the requirements below.
The base requirements to run Credential Guard on a platform are:
- Support for Virtualization-based security; requires a 64-bit CPU, CPU virtualization extensions plus extended page tables, and the Windows hypervisor (does not require the Hyper-V feature)
- UEFI Firmware version must be higher than 3.2.1.c, and UEFI Firmware must support UEFI secure update process. More information can be found at the Microsoft Hardware Compatibility Program Site.
- The computer must support and have secure boot enabled.
- At least a TPM of 1.2 is required, however a TPM 2.0 is preferred so Credential Guard can use hardware binding. This protects against attacks where the attacker has physical access.
- UEFI lock is also preferred as it prevents turning Credential Guard off via a registry edit.
- Windows Operating system version must be: Windows 10 Enterprise, Windows 10 Education, Windows 10 IoT Enterprise, or Windows Server 2016 (Note: Credential Guard is not supported on Windows Server running as a Domain Controller)
Enabling Credential Guard with GPO:
After creating a GPO for Credential Guard navigate the Group Policy Editor to Computer Configuration | Administrative Templates | System | Device Guard
The policy you will want to enable is Turn on Virtualization Based Security
Credential Guard in action
With Credential Guard enabled the password hashes are protected. When an attacker is able to trick the end user into running the malicious software instead of getting the password hashes they desire instead the attacker only gets the encrypted unknown key. The credential hashes are protected from being read directly as the hashes are protected securely in the virtualized credential store.
Credential Guard appears to be a great security tool; so what’s the catch?
As we stated before, Credential Guard is only available to those using Windows 10 Enterprise. So what can you do to protect your systems if you do not have Windows 10 Enterprise, or if you want to increase your defense in depth strategy?
PolicyPak Least Privilege Manager and SecureRun
While protecting the credentials from malicious software is a good option, what if you could prevent malicious software from running in the first place?
With PolicyPak SecureRun, you can! SecureRun does the job of a complicated whitelisting policy without the complication!
Let’s create a secure run Policy and then check back in with the program that steals credentials.
Create a new GPO, expand the Computer Configuration node, expand the PolicyPak node, select Least Privilege Manager, and add a new SecureRun Policy.
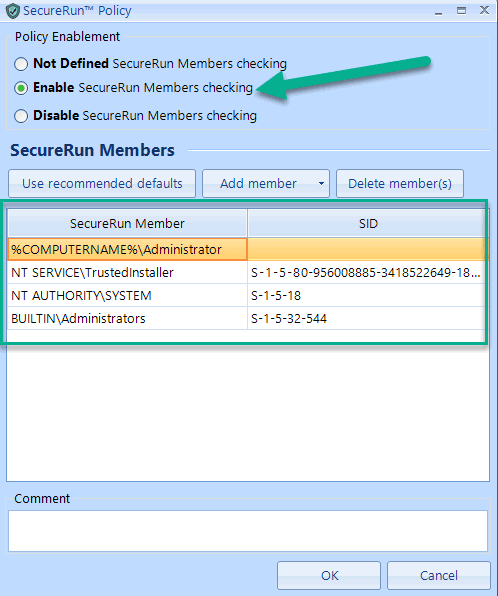
Enable SecureRun Member checking and select the SecureRun Members.
How does SecureRun work? SecureRun checks the file owner of the program against the user list you specified in the policy.
SecureRun in Action
Programs that are authorized to run and legitimately installed by the Admin, or via SCCM or something similar will show up like this. Here’s an example of a properly-installed application like Adobe Reader.
But the downloaded-by-a-user program which is malicious gets automatically blocked thanks to PolicyPak SecureRun. The file owner is our Finance user; he’s not on the SecureRun list, and hence the application will not run.
To see PolicyPak SecureRun in action check out this video.
Final Thoughts
There are many facets to an effective security policy. The main goal is to protect credentials and the data they are used to access.
SecureRun makes it easy for you to limit users to running only approved software. No more complex hard to maintain whitelists or blacklists. SecureRun stops malicious programs, keeping the bad guys out, and keeping your user base running only safe, approved applications. See some videos on SecureRun and Least Privilege Manager https://www.policypak.com/components/least-privilege-manager/