Jeremy Moskowitz founded PolicyPak Software after working with hundreds of customers with the same problem they couldn’t manage their applications, browsers and operating systems using the technology they already utilized.

Windows 10 Join Domain: Workplace vs Hybrid vs Azure AD
For Windows 10, joining a domain provides multiple options. As the workforce changes, and enterprises and applications evolve, there is a growing need to provide applications seamlessly to an ever-growing mobile workforce. Since cloud technology is becoming more prevalent in the industry, we will look at four ways to manage devices and applications that are “joined” in a variety of ways. In this article, we’ll explore a series of tweets with screenshots from @jandreacola that explain each method.
The methods we’ll explore here are:
- Traditional on-premise domain-joined devices
- Workplace-joined devices for your own device solutions
- Hybrid devices joined both on-premise and to Azure AD
- Pure Azure AD cloud-joined devices
Let’s check out each one and see how each method works.
Domain-Joined Devices
Devices managed in this manner are traditional, “on-prem” domain-joined devices. These machines rely on the enterprise’s on-premise equipment to deliver applications, identity, and management. A domain-joined environment means:
- Devices are Windows 10 joined domain via the company’s on-premise Active Directory Domain.
- Users can log in to any device in the enterprise by default.
- A user logged into the domain has Single Sign-On (SSO) access to on-premise applications and resources.
- When devices leave the enterprise network, a VPN is required to access on-premise services.
These points are illustrated in the screenshot below.
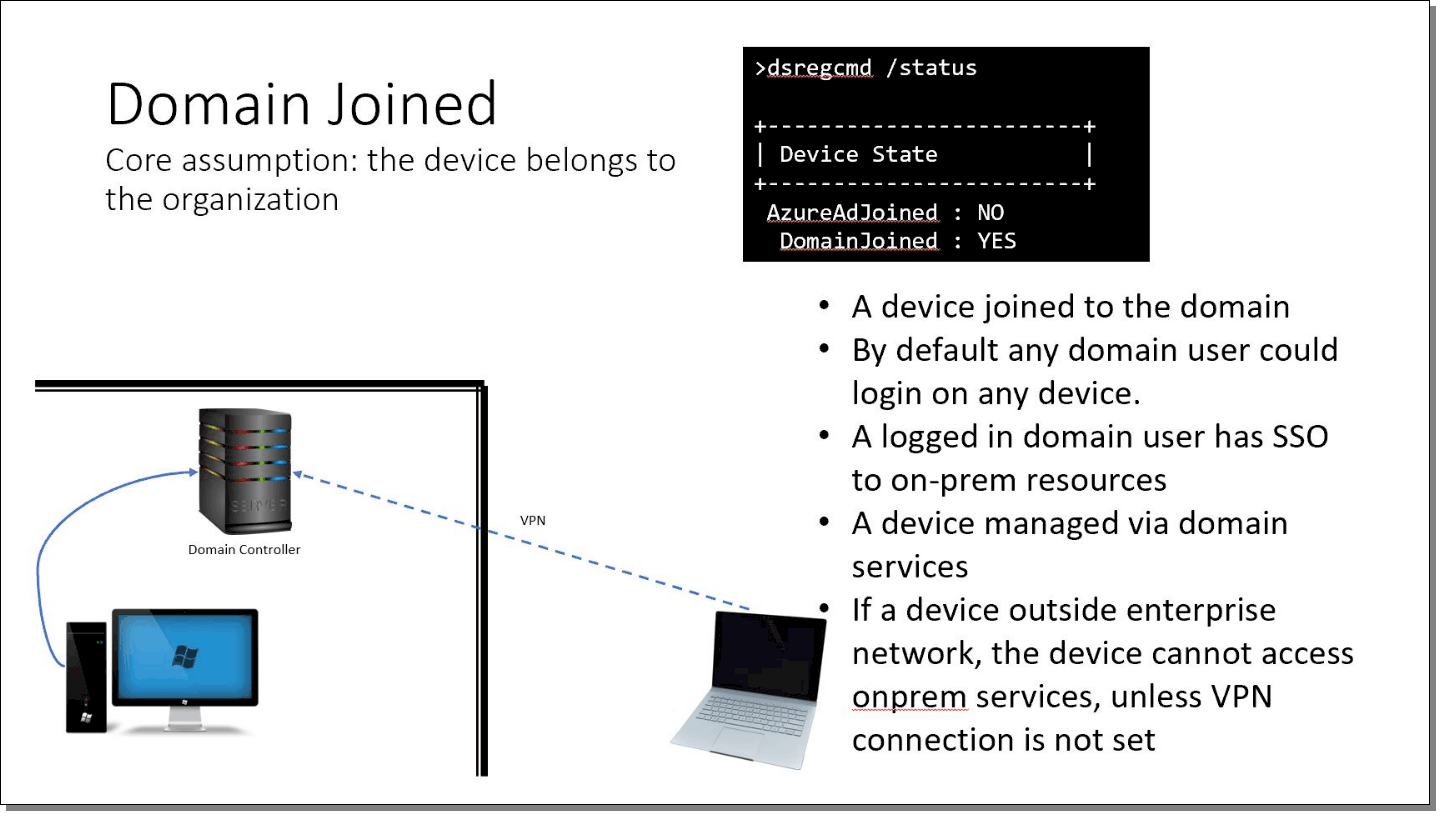
Image Credit: Julie Andreacola https://twitter.com/jandreacola/status/1226183342833459203
The classic domain-joined model is what most organizations use, and it works well for most circumstances. Of course, getting Group Policy settings requires being domain-joined; but GPOs will download over a VPN if on the endpoint.
Note in the screenshot the dsregcmd /status command, which shows the following status:
- AzureAdJoined = No
- DomainJoined = Yes
When you see this precise combination, the machine is pure-play domain-joined with no Azure or other cloud involvement.
The following are some of the benefits to the traditional domain environment:
- Can be very cost effective as licensing is usually perpetual
- Easily supported and many professions are very familiar with the traditional domain
- Easy out of the box management of endpoints
However, some of the disadvantages of a traditional domain environment include:
- Access to apps outside of the environment typically requires a VPN
- A hardware refresh cycle for servers must be maintained
- A large capital expenditure can be required
Workplace-Joined Devices
A workplace-joined device allows users to access company cloud resources, with or without mobile device management (MDM). The basic idea behind workplace join is for a user to walk in the door with his or her own laptop and get some credentials supplied by you, the IT admin. Once workplace-joined, the user has access to the company’s specific web applications via SSO.
For instance, if you wanted to hire some seasonal, freelance sales workers this scenario works perfectly. They show up with their laptops and you hand over their credentials. They perform their own “workplace join.” Then immediately after that, they are able to use your sales application with their credentials. When you say goodbye to them, you disable their account, and they lose their access.
Some of the main attributes of workplace join include the following:
- The device is not joined to the company domain and is usually owned by the user. This could be a BYOD scenario, a student brining his or her own laptop to a college campus, a temporary contractor, or any other temporary worker.
- The workplace-join state is specific to the currently logged on user.
- The user logs in with their Microsoft account or an account local to the machine.
- The user has SSO access to cloud resources from that logon session; different user accounts from the same device will not have SSO.
- MDM is optional to the user. The user can opt-out of some MDM features, limiting resources the user has access to.
These points are illustrated in the screenshot below.
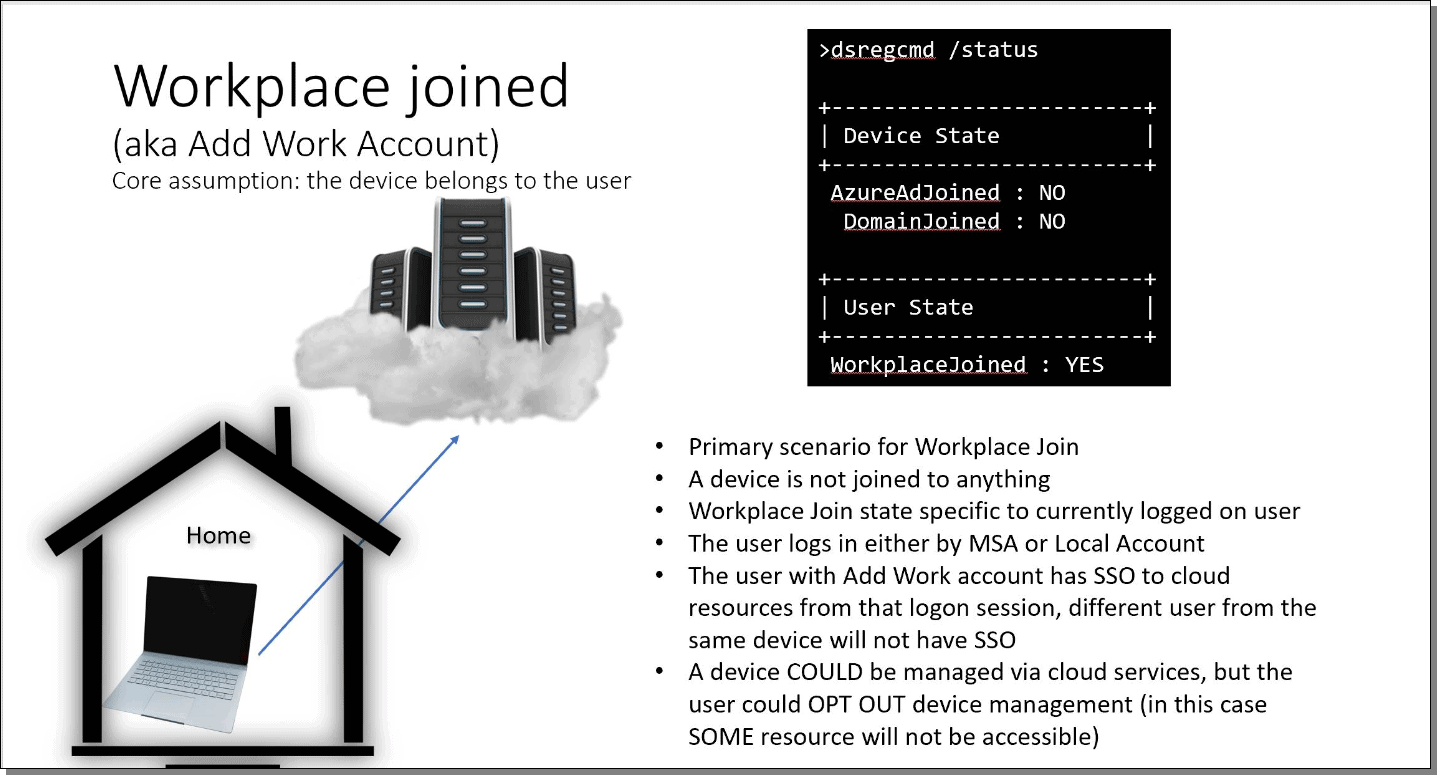
Image Credit: Julie Andreacola HTTPS://TWITTER.COM/JANDREACOLA/STATUS/1226184803076263936
Workplace join is a good option for enterprises that have staff who work from home or that have a base of outside contractors who are not provided with company equipment. In these cases, you cannot really manage their machine (nor would you want to), but you can grant or revoke access to web applications (think Salesforce or Box, etc.).
Note in the screenshot the dsregcmd /status flags:
- AzureAdJoined = No
- DomainJoined = No
- WorkplaceJoined = Yes
You can see how to perform a workplace join domain Windows 10 with this walkthrough: https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/operations/walkthrough–workplace-join-with-a-windows-device.
The following are some of the benefits to workplace join:
- Minimal company equipment required
- Easy to allow access to company applications and data
- Minimal training required
Some of the disadvantages to workplace join include:
- Limited overall control of end-user devices
- IT may have to look at devices not in a typically desired state
- End user complaints or refusal to use BYOD due to the company having access to the device
Hybrid-Joined Devices (Domain-Joined and Azure AD-Joined)
Azure AD hybrid join is a configuration that many organizations are moving to in which the devices are joined to the enterprise’s local Active Directory Domain and their Azure AD tenant. Hybrid-joined environments have the following attributes:
- The device is joined to both the enterprise’s local domain and the Azure AD cloud.
- By default, any domain user can log in to any device.
- The logged in user has SSO to both cloud and on-premise applications.
- The device can be managed by both cloud services and local domain services.
- When a device is outside the enterprise network, the device will still be able to access cloud services, and the admin can still manage the device via cloud services.
- The device will still need a VPN to access any services hosted on-premise.
- The VPN can be a cloud-based VPN solution.
These points are illustrated in the screenshot below.

Image Credit: Julie Andreacola HTTPS://TWITTER.COM/JANDREACOLA/STATUS/1226185444418871298
Many organizations are moving to the hybrid model, supporting classic on-premise applications while adopting more cloud applications and solutions. However, moving too quickly to this model could be a mistake since once you hybrid join a machine, you can’t undo it.
Note in the screenshot the dsregcmd /status flags:
- AzureAdJoined = Yes
- DomainJoined = Yes
If you want to learn more about hybrid-joined devices (and what they look like right after they’re hybrid enrolled), this is a good blog article: https://oofhours.com/2020/01/20/the-first-day-in-the-life-of-a-hybrid-azure-ad-joined-device/.
The following are some of the benefits using hybrid join:
- Devices and users can have SSO to on-prem and cloud applications
- Devices can benefit from being cloud managed as well as managed with traditional AD management tools such as Group Policy
- Access to powerful logging and reporting tools native to Azure, like Desktop Analytics or Windows Update Compliance, without SCCM
Some of the disadvantages to hybrid join include:
- Increased costs and maintenance of the traditional domain-joined environment as well as the Azure Cloud environment
- Access to on-premise resources still requires the use of VPN or remote access tool
- Increased administrative burden and more complications in deployment and support
Azure AD-Joined Devices
In the final screenshot below a special keyword should be noted: “North star.” This phrase is an internal rallying cry at Microsoft expressing their final recommended state for customers. In other words, all things being equal, this is the way Microsoft would want you to design your worlds.
Azure AD join domain windows 10 machines connect directly to the enterprise’s cloud without on-premise infrastructure. The environment has the following attributes:
- Termination of any final on-prem domain controllers.
- Global state of the device, the entire device is joined directly to the cloud.
- By default, any user can login to the device.
- A logged-in cloud user has SSO to cloud resources on that device.
- Cloud services manage the device.
- Basically, everything is in the cloud: the management platform, the device registration, and the admin console.

Image Credit: Julie Andreacola https://twitter.com/jandreacola/status/1226183781511520257
If you want the flexibility of having this kind of all-cloud environment in the future, you should plan for it now. As I mentioned in the previous section, once you hybrid join a machine (that is, join it to Azure AD and on-prem AD), there is absolutely no way to roll back the machine to being only Azure AD-joined without completely reformatting the machine.
The following are some of the benefits of using Azure AD join:
- Very flexible cloud deployment, no restrictions by traditional on-premise systems, and low or no capital expenditure
- Access to data and applications from anywhere with no VPNs required
- Management of the environment from anywhere using cloud tools like Intune
Some of the disadvantages to Azure AD join include:
- While there are no upfront server costs, monthly cloud costs can be surprising and should be closely monitored
- Cutting or bleeding edge cloud deployments can have limited or more specialized support required
Final Thoughts
As cloud technology evolves, admins have many more options for managing their endpoint devices. Admins now have access to the traditional management solutions included with on-premise installs, Active Directory, and Group Policy but can also manage devices and provide applications from the cloud to devices located anywhere with Azure AD and Intune, as well as securely delivering applications and resource access to devices that are not company owned. Additionally, you can bring PolicyPak into on-prem, hybrid, or cloud-only deployments to get superpowers you cannot get with Group Policy, Intune, or any other MDM.
For more on managing the Modern Desktop and more on using these methods, check out my books: Group Policy: Fundamentals, Security and the Managed Desktop and MDM: Fundamentals, Security and Modern Desktop at https://www.mdmandgpanswers.com/books.
Thanks to Justin Hart for additional help with this blog entry.


