Jeremy Moskowitz founded PolicyPak Software after working with hundreds of customers with the same problem they couldn’t manage their applications, browsers and operating systems using the technology they already utilized.

5 Tips for Windows 7 End of Life That’ll Simplify Windows 10
Windows 7 End of Life
The Windows 7 end of life date is soon approaching, and many organizations are analyzing, planning and implementing their Windows 10 migration. Although Windows 7 is considered the most popular Windows operating system, Microsoft will end Windows 7 support, including patches and security updates on January 14, 2020. As organizations scramble to make sense of their Windows 7 end of life strategy, many administrators, system engineers, and IT architects still don’t understand all the technical and business nuances of migrating to Windows 10. As a result, we wrote this blog post to answer frequently asked Windows 7 end of life questions and help IT practitioners prepare for the challenges of migrating to Windows 10.
When is Windows 7 End of Life?
For those unfamiliar with the Microsoft support model, the company offers two support periods: mainstream support and extended support.
Windows 7 End of Life Support
| Support Period | Windows 7 End of Life Date |
|---|---|
| Mainstream Support | January 13, 2015 |
| Extended Support | January 14, 2020 |
Windows 7 Mainstream Support
The first type of support is called mainstream and typically lasts for five years. During this span, Microsoft provides regular feature updates, design changes, warranty claims, patching and security updates. Mainstream support for Windows 7 reached its end of life on January 13, 2015.
Windows 7 Extended Support
Since mainstream support ended, Windows 7 had been covered by a type called “extended support.” This level of support includes continued patching for bugs as well as security updates. Although there isn’t any functional innovation during an “extended support” period, the OS remains safe to use.
On January 14, 2020, Microsoft plans to terminate extended support for Windows 7. Once extended support expires, Windows 7 will no longer have any official support. All organizations will be forced to upgrade to Windows 10 or accept the risk of using an unsupported operating system.
Windows 7 End of Life Trends
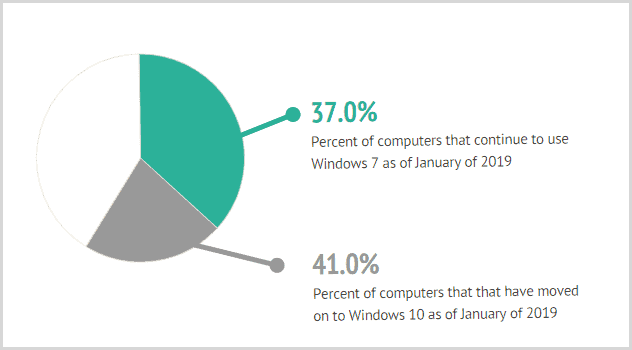
It has been a heck of a ride for Windows 7. Even though mainstream support ended more than four years ago, many organizations still use it. As of January 2019, 37 percent of computers continue to use Windows 7 while 41 percent have moved on to Windows 10. In a 2018 survey, 43 percent of IT professionals said that their company is still running Windows 7 to some extent. That same survey found that 17 percent of businesses were not even aware that support was ending. Above all, there is a significant presence of Windows 7 out there in the world, and that poses a security threat for many organizations.
Windows 7 End of Life Security
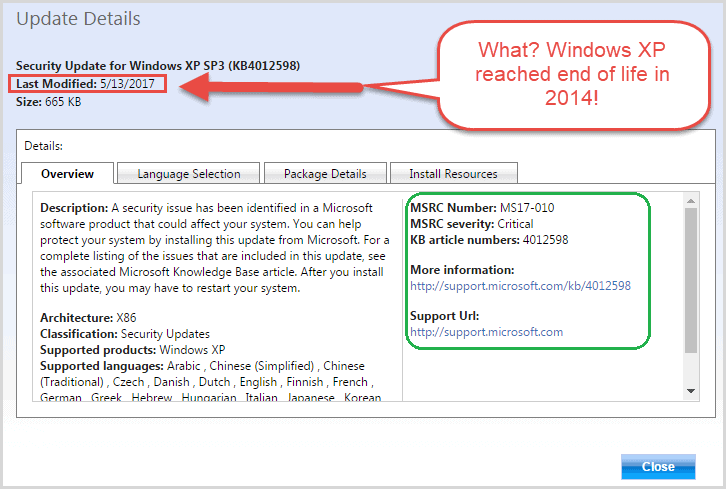
If you are one of the remaining Windows 7 loyalists, you should understand that using an unsupported operating system poses serious security risks. Hackers and other criminals in the cyber community will target Windows 7 machines as new vulnerabilities are discovered. Rather than continuing with Windows 7 after its end of life date, you should upgrade to the fully supported and patched Windows 10 operating system. Cybercriminals to this day target the unsupported XP machines that are still in existence.
The global malware outbreaks of WannaCry and NotPetya wreaked havoc on companies and organizations all over the world throughout the middle of 2017 by taking advantage of the well-known exploit called EternalBlue. This vulnerability was so severe that Microsoft released a patch even though extended support had reached its end of life years beforehand. Unfortunately, the patch required a manual update, and to this day, many unpatched XP machines run in a highly vulnerable state. In summary, non-supported operating systems like Windows XP or Windows 7 are vulnerable to exploits by dangerous cyber criminals.
Windows 7 End of Life and Simplifying Windows 10
If you’re looking to migrate to Windows 10 before Windows 7 end of life, now is a good time to start your preparations. Although the Windows end of life support date is in January 2020 and may seem like a long way off, there are many differences between Windows 7 and Windows 10 to analyze and understand. To help you out, we’ve put together a list of tips and PolicyPak solutions you could use to simplify your transition to Windows 10.
- Windows 7 file associations are different than in Windows 10
- It’s time to master start-menu and taskbar customization
- Employees like using multiple browsers. Deal with it
- Java…Please don’t forget about Java compatibility
- Time to kill local admin rights and elevate user privileges
Tip #1: Windows 7 File Associations Are Different Than in Windows 10
We covered this topic in an earlier blog. The post outlines the significant differences found between Windows 7 vs. Windows 10. For starters, Windows 10 does not handle file associations in a way that’s easy and familiar. For example, Windows 10 matches PDF files with the Edge browser and email defaults to the Windows 10 Mail application instead of Microsoft Office. In a recent Windows 10 Migration survey, 63 percent of all organizations admitted they were challenged by Windows 10 file associations. 57 percent of those organizations said they are either updating file associations manually or letting users manage file associations themselves.
To simplify Windows 10 file associations, try PolicyPak File Associations Manager
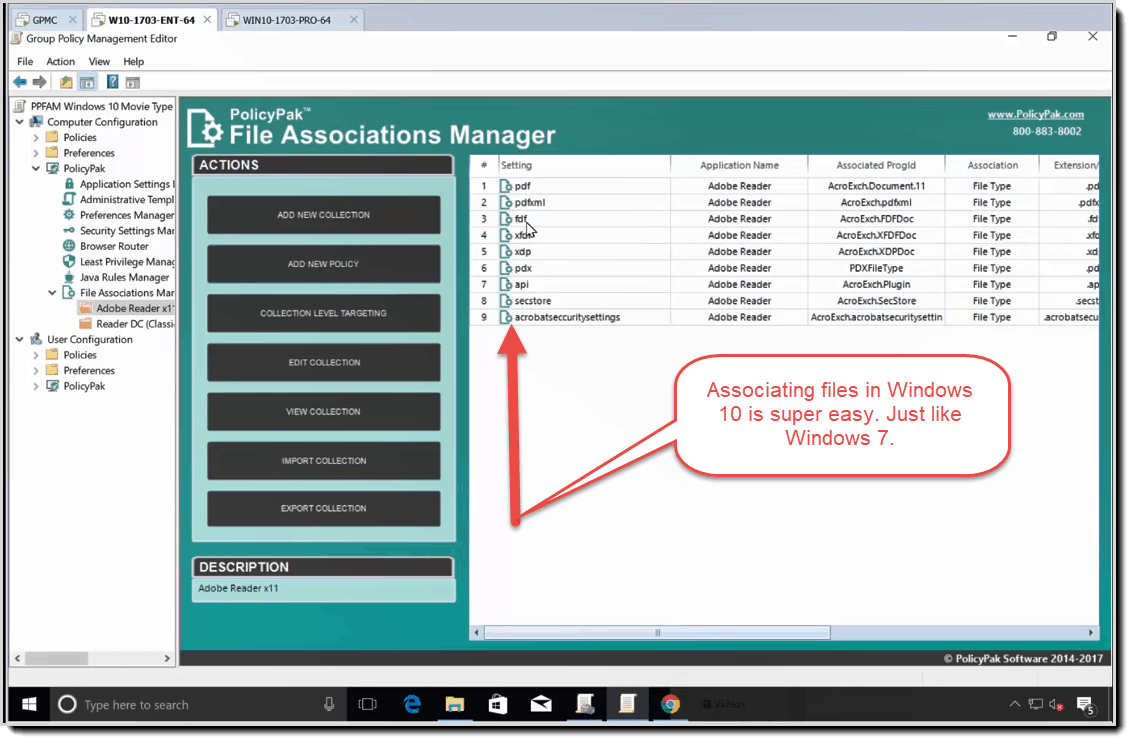
This Windows 10 file association management tool lets you dictate which file opens in what application. The tool also lets you update any file association instantly whenever your needs change. Once Windows 7 end of life has come and gone, you can use this tool to simplify file associations in Windows 10.
Managing Windows 10 file associations
Getting Windows 10 to work with file associations can be a pain. Just mapping a PDF to work with Acrobat and MAILTO to work with Outlook can be a challenge with Windows 10. This mapping used to work great in Windows 7 with Group Policy, but not anymore. To fix file associations with Windows 10, you need PolicyPak File Associations manager, which you can see in this demo.
Tip #2 – It’s Time to Master Start-menu and Taskbar Customization
The Windows 10 Start Screen Menu and Task Manager have come a long way since Windows 7 and offer a lot more customization. Consequentially, they also present distinct challenges for those who want to standardize start screen and taskbar usage. According to our Windows 10 migration survey, companies are overcoming this challenge using a combination of Group Policy, SCCM, scripts, and third-party tools. However, many of these solutions only work in traditional AD environments, which leaves those hosting computers in Azure out to dry.
To Simplify the Windows 10 start screen and taskbar, try PolicyPak Start Screen and Taskbar Manager
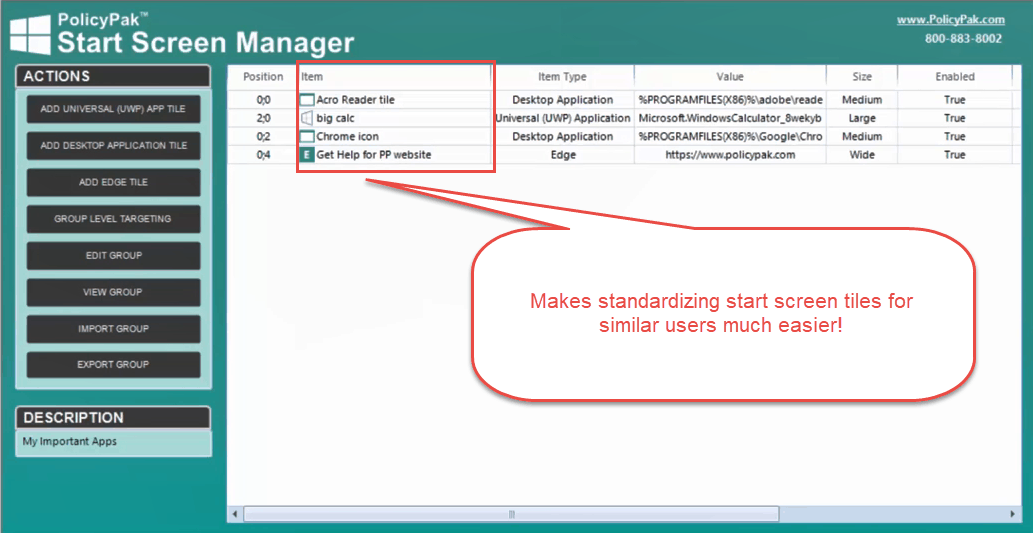
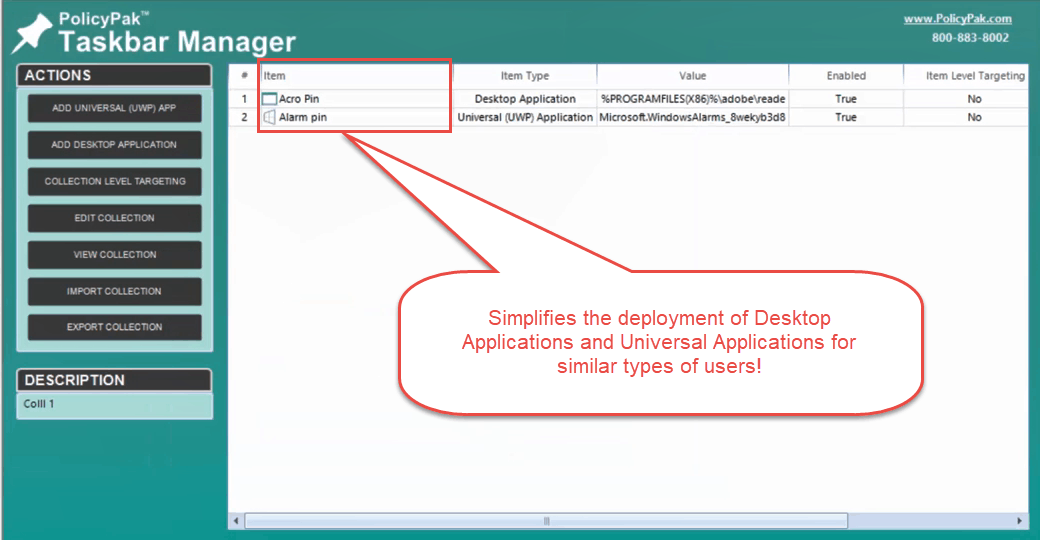
These convenient tools enable you to customize and lock down tile formations within the Windows 10 Start Screen and pin or remove applications in the Taskbar for all of your devices. The tools also leverage Item Level Targeting from Group Policy Preferences, which allows you to assign policies that deliver granular settings.
Managing the Windows 10 Start Screen
The Windows 10 start menu is confusing to configure centrally. However, PolicyPak enables you to dictate which applications users have within their start screens. For example, you can add the Windows desktop, universal apps or Microsoft Edge tiles to corporate groups. You can also remove or maintain the user’s existing groups. The short video below demonstrates how to standardize all Windows 10 start menus.
Managing the Windows 10 Taskbar
Providing users with quick access to business-critical apps is vital for optimal productivity. With PolicyPak, you can programmatically associate icons to the Windows 10 taskbar quickly and easily. With PolicyPak and PolicyPak Start Screen & Taskbar Manager, its easy to draft then deploy your start menu via Group Policy, SCCM or your MDM service.
Using Item Level Targeting To Determine “Who Should Get What” Start Menu Items
Ensuring similar users have the same start menu items is pretty complicated in Windows 10. Fortunately, PolicyPak allows you to add or remove icons based upon conditions automatically. For example, you can specify “who should get what” settings based upon conditions like security group, laptop vs. not laptop and so on. The video below demonstrates how you can deliver different groups of icons to different people.
Tip #3 – Employees Like Using Multiple Browsers. Deal With It.
While Windows 10 introduces some unique challenges, it’s also saddled with some of the same issues that admins have dealt with for years. For instance, how do you deal with multiple web browsers battling one another for default browser status? Alternatively, how are you ensuring that a particular web browser is the only one used for designated websites?
To overcome Windows 10 browser management challenges, try PolicyPak Browser Router
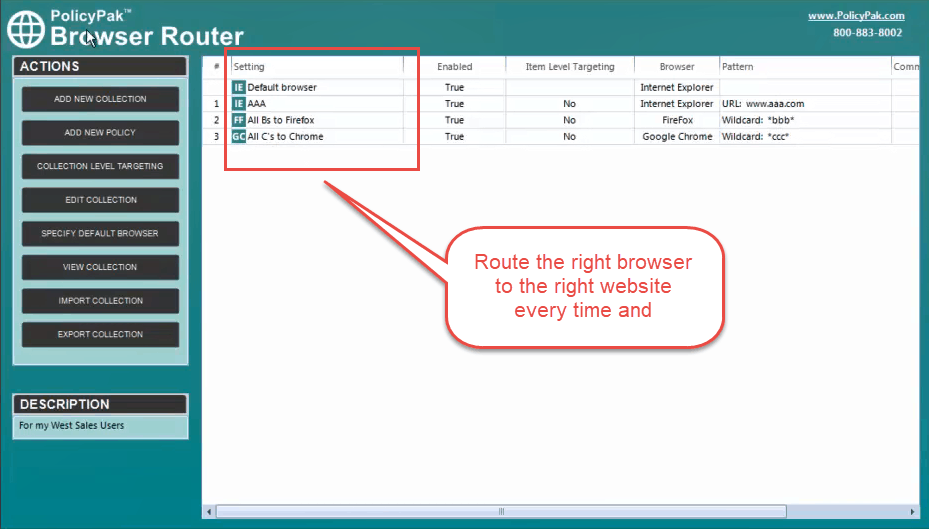
This component enables you to block unauthorized websites, manage IE compatibility and force a default browser whenever a user has multiple browsers. You can also map websites to browsers, which forces the correct browser to be used each time.
Controlling Browser Choice in A Multi-browser Environment
With PolicyPak Browser Router you can automatically launch whichever browser you mandate on a website-by-website basis. For example, force websites to load in the most compatible and secure browser. Everyone knows that not every browser is right for all websites, and employees use the wrong website most of the time. The video below demonstrates how PolicyPak Browser Router lets you create policies (or routes) where designated websites are opened only into specific browsers.
Blocking Access to Unauthorized Websites
One way to enforce corporate mandates is to limit access to dangerous and inappropriate websites. As such, PolicyPak Browser Router prevents users from visiting websites that don’t have your approval. Here is a video that shows how to both block and allow specific websites.
Managing Internet Explorer 11 Compatibility and Enterprise Modes
Managing compatibility and enterprise modes for IE 11 with Group Policy is complicated. Fortunately, you can use PolicyPak Browser Router to set Enterprise and Document modes based on the website dynamically. This video shows how you can dynamically configure those modes.
Tip #4 – Java…Please Don’t Forget About Java Compatibility
Managing Java environments for newly-provisioned computers require thought and careful planning. As such, your migration to Windows 10 could present some Java compatibility issues.
To simplify Windows 10 Java version management, try PolicyPak Java Rules Manager
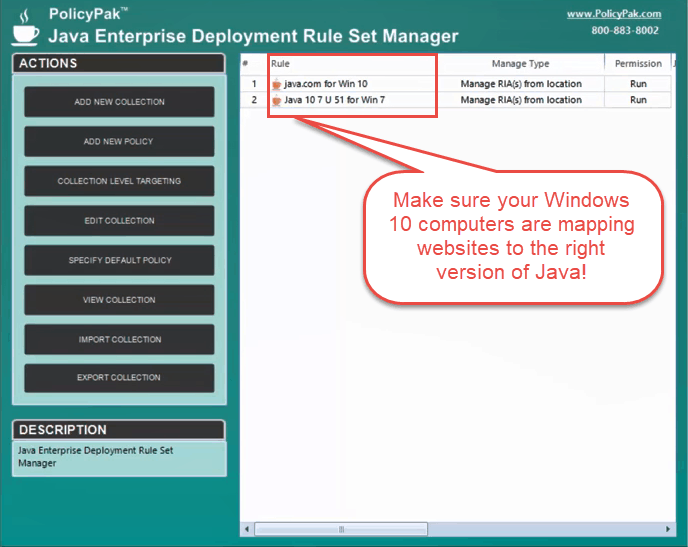
PolicyPak resolves Java management issues by automating Deployment Rule Sets. Generally speaking, some websites use Java for malicious intent while others use Java for legitimate business purposes. With PolicyPak Java Rules Manager, you can prevent dangerous websites while still allowing the legitimate ones to render (per browser). Additionally, since you often need to dictate the right version of Java for a particular website, this becomes “point and shoot” easy for PolicyPak Java Rules Manager.
Creating and Deploying Java Deployment Rule Sets
Your migration to Windows 10 may complicate which versions of Java are deployed in your environment. The video below demonstrates to map specific websites with Java applets to specific versions of Java.
Blocking All Websites That Use Java While Creating Some Exceptions
Your organization may have legacy applications that rely on Java to function. However, you may also want to block all websites from using Java, unless you had approved of them. The video below demonstrates how you can ensure all Java websites are blocked but still allow (and map) approved websites.
Tip #5 – Time to Kill Local Admin Rights and Elevate User Privileges
Your migration to Windows 10 provides the perfect opportunity to implement best practices for least privilege management. Protecting against trojans, ransomware, and other malware is arguably more important now than ever, and allowing users local admin access after the Windows 7 end of life date is a recipe for disaster.
To manage Windows 10 user permissions and get away from local admin rights, try PolicyPak Least Privilege Manager
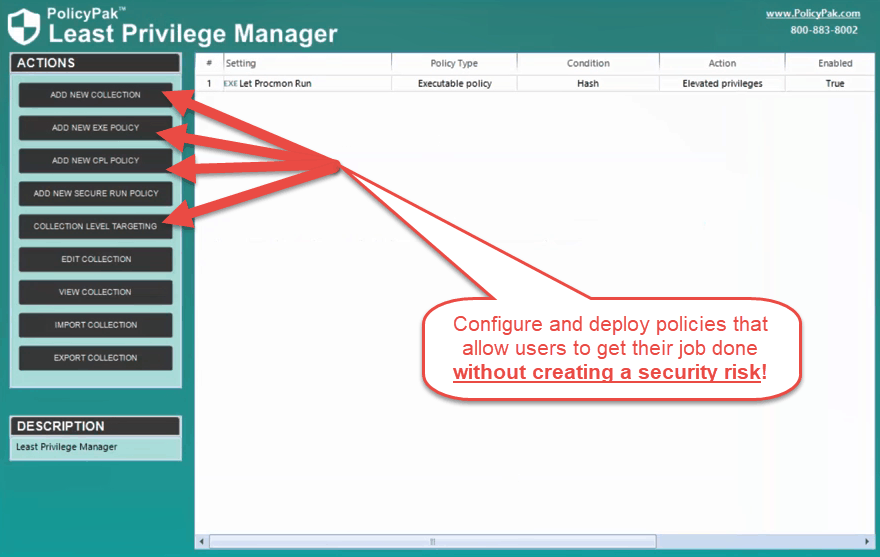
With PolicyPak Least Privilege Manager, you have the power only to provide users the permissions required to do their job. For example, you can elevate only the applications users need or enable standard users to bypass UAC prompts.
Killing Local Admin Rights and Bypassing UAC Only On Applications
You don’t have to provide all users with local admin rights to get their job done. PolicyPak Least Privilege Manager elevates only the applications that Standard Users need to run. The video below shows how you can balance security with productivity using the least privilege model.
Preventing Malware, Ransomware, and Malicious Zero-Day Threats
Cryptolocker, ransomware and other malicious software are downloaded and installed by standard users all the time. However, blacklisting is impossible because there are thousands of malicious applications created per day. Similarly, whitelisting isn’t easy either. You would have to stay abreast of every application you deploy and install continuously. Fortunately, PolicyPak SecureRun only lets applications run if they were “properly installed” or otherwise approved by you. This video demonstrates how to implement and use the SecureRun feature.
Controlling Application Installation
If you’re looking for secure application control to block malware and exploits, PolicyPak Least Privilege Manager does the job in just a few clicks. The component enables you to specify what executables, scripts, Java, MSIs and other types of files will run. You can even block scripting tools like PowerShell and Command Prompt (CMD).
Windows 7 End of Life is Almost Here. Get Started with PolicyPak Today.
With PolicyPak, your migration to Windows 10 doesn’t have to be a struggle. PolicyPak is comprised of components that allow you full control of Windows 10 desktops for all of your devices and users. What’s more is that you can deploy PolicyPak through your MDM service (like Microsoft Intune, VMware Workspace One, and MobileIron), endpoint management solution (like Group Policy, SCCM, Altiris and KACE) and to non-domain users via the Cloud. Although Windows 7 may be approaching end-of-life, you can use these tips and tools to ensure a smooth transition to Windows 10.
To get started, visit PolicyPak.com and sign up for a free trial
During this time, a PolicyPak technical specialist will be available to ensure that Windows 10 is as easy to manage and secure as Windows 7. Likely easier.


