Justin Hart is the IT director for an automotive group specializing in Recreational Vehicles. As the IT Director in a Medium Enterprise, he wears many hats, including running a small helpdesk, being the Systems and Network administrator as well as managing the department. He is very passionate about Windows networks, Active directory, Group Policy and managing enterprise environments where these technologies are employed. He is an top contributing, active helper on the Spiceworks forums. In his spare time, Justin enjoys cooking, attempting to play golf, camping, and the outdoors

Windows Update for Business (WuFB): A Simplified Guide
Let’s talk about Windows Update for Business. Windows updates are one of the significant responsibilities of a Windows systems administrator. Without updates, you leave your systems vulnerable to attacks, bugs, and merely staying behind.
The question is: How do you manage Windows updates in the ever-changing landscape that is the “always on the go” office of today?
Well, there are a few options:
- Option 1: Just let Windows handle it. This sounds automatic and great. But if you have an update that is incompatible with your workforce, 100% of your users are going to be calling you saying that their Windows 10 is broken. Its best to leave automatic updating for the “one-off” machines in your environment, but not the majority.
- Option 2: Windows Server Update Services (WSUS). Upsides? It’s been around for a while, and it works. It remains a good option if you have a traditional brick and mortar business and also have the administrative staff to manage the servers and all the testing, plus the burden to approve updates. This technique does leave out the road warriors and those always on the go.
- Option 3: What if there were something in-between “total automatic updates” and “manually managing each update”?
Introduction to Windows Update for Business
Enter Windows Updates for Business or WuFB (pronounced WOOF-be.. yes, really !).
Windows Update for Business allows an administrator to define Windows Update servicing rings. These are admin-defined groups of machines where you can pre-test some updates and decide how quickly they receive updates.
A typical set of rings would include:
Your “testing” ring: This ring would have no delay in updates. As soon as they are released, a ring of initial computers would receive the updates to test. Just like your manual testing group in WSUS, but it is automatic. Your “pilot” / “canary” ring: The next ring would include a few more systems, a broader deployment group, but still a smaller subset of a larger group of systems. This group would be set to defer the updates for a few days after the initial group would receive the updates. Your “rollout” ring: typical third ring in the set would be the remainder of the systems in that grouping. This ring would be set to defer and install a few days after your second ring.
How do you set up and apply these rings to Windows 10 computers? Through GPO, of course.
What’s the best practice to select which Windows 10 computers should end up in what ring? You can take some volunteers that are more tech-savvy for your “testing” ring. But it’s a good idea to, generally, put your most forgiving people in the “testing” ring, but you also need a broad enough sample to represent your whole company’s Windows 10 population.
So why rings? These rings allow an automated way of pushing out updates to test groups and pausing them if something doesn’t sit well with your environment.
You can pause (really, defer) updates for each of your rings for 35 days with just the simple check of a box.
This gives the ability to pause or defer updates like WSUS but without clients having to talk to the WSUS server to approve and download updates.
Why is this beneficial? Using WuFB automates the update process for those who don’t either have the staff or the resources to manage a WSUS or SCCM environment. It automatically runs until you realize there is some problem, which you can react to; instead of testing every configuration with every patch from WSUS. So, you get the best of both worlds.
Setting Up and Building Out WuFB Rings
Let’s take a look at some Windows Update for Business rings that you can use in your environment.
You can have as many rings as you want/need for your environment, but a typical deployment might have three rings for each group of computers. Something that looks like this:

Let’s see how to create a ring or two
In this example, I have gone into the GPMC. I am going to make three GPOs, one for each ring for my OU of Computers in Engineering. The policy settings for WuFB are Computer side settings.
I’ll call these GPOs:
CP-WUFB-Testing: This ring will be the group of your initial testing computers that you selected.CP-WUFB-Pilot: This ring will contain a broader group of your testing computers.CP-WUFB-Rollout: This ring will contain the rest of the production machines for the Engineering OU.
This corresponds to the graphic earlier, where I’m putting some portion of my population into each group. So the Engineering computers in the Central OU will be my first to get the Windows Update for Business settings.
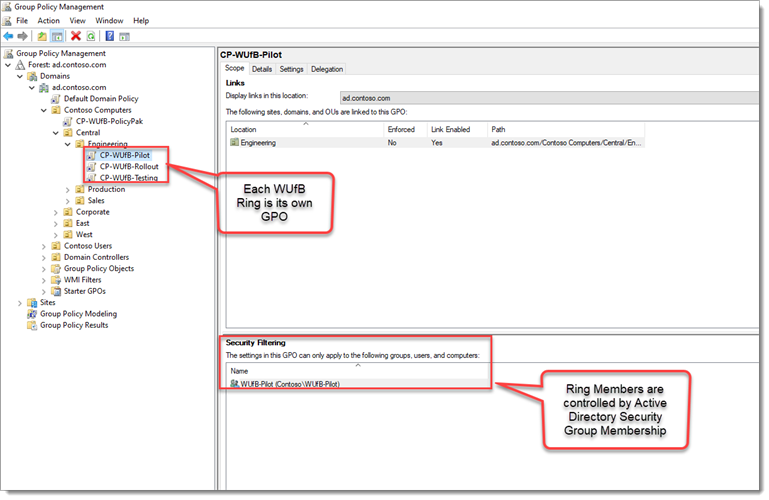
Note that in our examples, we’re creating rings only for the Engineering computers. You should likely do this same procedure for your other key OUs; for instance, in my example Sales, Production, Corporate, and so on.
After you create the GPOs, each of the rings will be controlled by regular Active Directory Security Groups. Group Policy Security Filtering will apply to GPO to the Testing, Pilot, and Rollout rings depending on group membership.
Groups are one way to apply the rings. Different OUs for each ring would be another option.
Windows Update for Business Settings
Now let’s take a look at the Windows Update for Business settings themselves.
They are located under Computer Configuration |Administrative Templates | Windows Components | Windows Update | Windows Update for Business
Preview Builds and Feature Updates
First, we configure the Select when Preview Builds and Feature Updates are received policy setting. You can see this policy setting here.

This policy setting controls what Release Channel the Computers should use. The Release Channel is a whole topic in itself, but in a nutshell, it is a setting that controls receiving official production build updates or less-than-stable Insider Updates. Insider updates are Microsoft’s beta testing program.
For our Rings, we will select the Semi-Annual Channel, which is appropriate for most businesses.
Build and feature updates can be deferred for up to 365 days; after that time, Windows will forcibly perform the build update and upgrade to the next version of Windows 10.
For our testing ring, we will want them to receive these as they are released for production.
Quality Updates
The other policy setting that we will want to set is for quality updates. The policy setting is called Select when Quality Updates are received. This will set up our acceptance of your monthly security and quality roll-up updates. Again for our testing ring, you will want to make these updates available without delay.

That settles the testing ring.
Pilot Ring
Now, what about the Pilot ring?
You’ll repeat the process, but you’ll be setting up your Pilot ring, so it is delayed by a few days. Before you get started to set the policy settings, first use the standard Group Policy security filtering to set the computers, which will be in the Pilot ring.

Simply edit the GPO and set the same policies, with slightly different values, to increase the delay before they get the updates.
The Pilot ring should also be on the Semi-Annual release schedule, but this time we will delay feature and build updates for 7 days, like this.
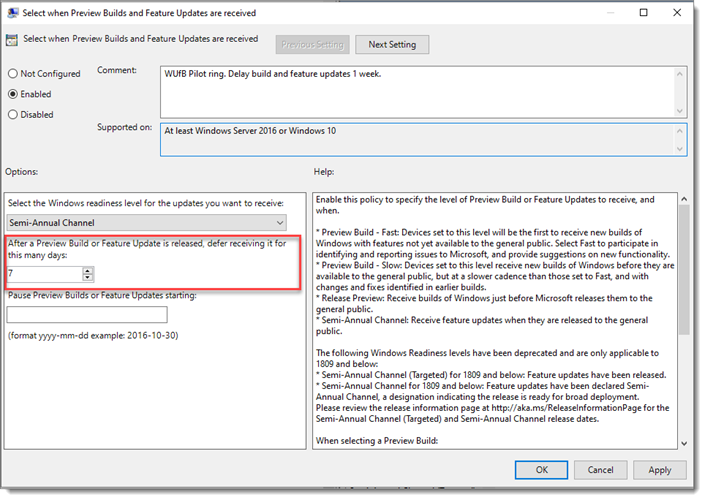
However, we will move a little faster with Quality Updates as we can only defer them up to 30 days rather than the 365 for build/feature updates.

Rollout Ring
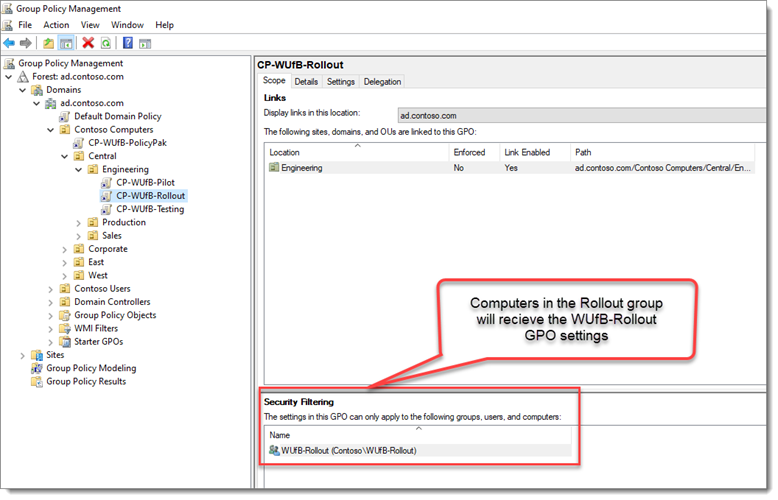
And lastly we will take a quick look at the Rollout ring update settings:
Again these will be governed by the slow ring group. Again, create the GPO then filter by group membership.
Here we will delay feature and Build updates by 30 days. To give us plenty of time to make sure the testing and pilot rings are operating fine.
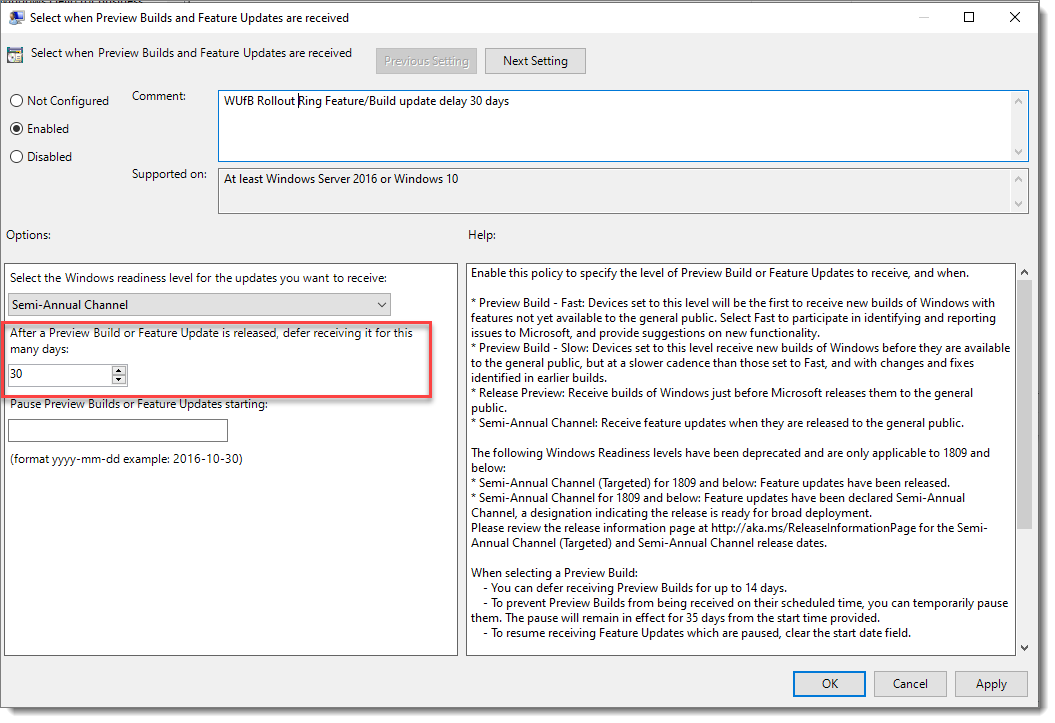
Quality Updates for the Rollout ring we will be set to defer7 days to ensure that there are no issues with the testing and the Pilot rings.

We all know that any company is not perfect, and Microsoft is no exception. So what happens if an update inadvertently affects a crop of our machines?
If we discover an issue with an update in our testing ring, where a user has reported an issue after the update, and it has been confirmed, then we can pause the update from being deployed.
So imagine that “Patch Tuesday” has come and gone, and “Oh my!” we have discovered that the latest quality update has caused an issue in the Testing ring.
Don’t panic!
You edit the GPOs of the Pilot and Rollout rings and pause the update from installing as they usually would. You enter the date to start pausing Windows Update, like so:
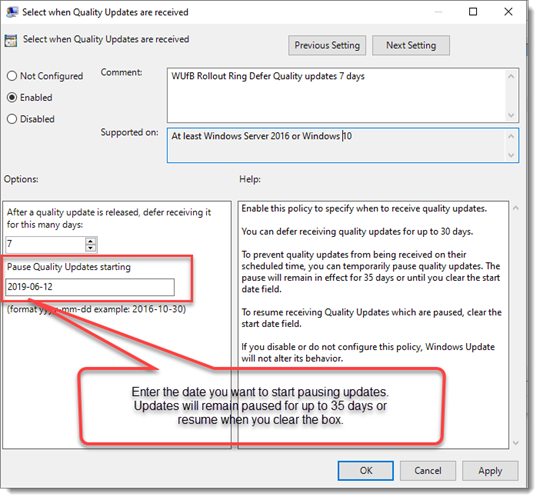
By entering a date in this field, we put Quality Updates on pause. Updates will pause for 35 days or until you clear the date box. Whichever comes first.
This allows you to test the update further or remediate any other issues in the environment that might be causing issues with the updates.
Windows Update for Business GPO Issues
So what struggles are there with Windows Update for Business?
Large Environments
I alluded to it before; what happens if you have a large environment? What happens if you want more rings to stagger bandwidth usage? WuFB uses Group Policy, and this could add up to many, many GPOs.
There has to be a better way, right? There is! PolicyPak Admin Templates Manager.
How does this help? Instead of having three, or thirty GPOs, you can compress all the GPOs into (quite literally) one GPO Using PolicyPak Admin Templates Manager.
Let’s take a look at how to do this with PolicyPak Admin Templates Manager.
Instead of creating GPOs for each OU and each ring in each OU We will create our new GPO at the computer root affecting all computers.

But inside the GPO, we won’t be affecting every computer.
Using Collections
PolicyPak Admin Templates Manager enables you to create Collections for each group.
A Collection is like a mini-GPO within the GPO! In this example, we’re creating a Collection just for our Central Engineering OU, for instance.
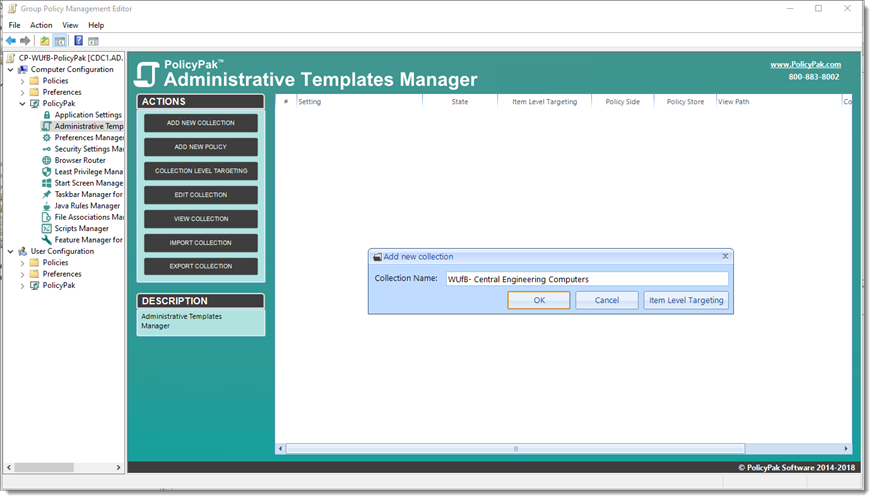
As we create the collection, we can target the Central Engineering OU.

Now that that collection is created, we can create our rings for that OU in that collection: one policy for each ring (Testing, Pilot, and Rollout.)
Here’s a finished example with all of our WuFB settings in a Collection … instead of creating a whole new GPO!
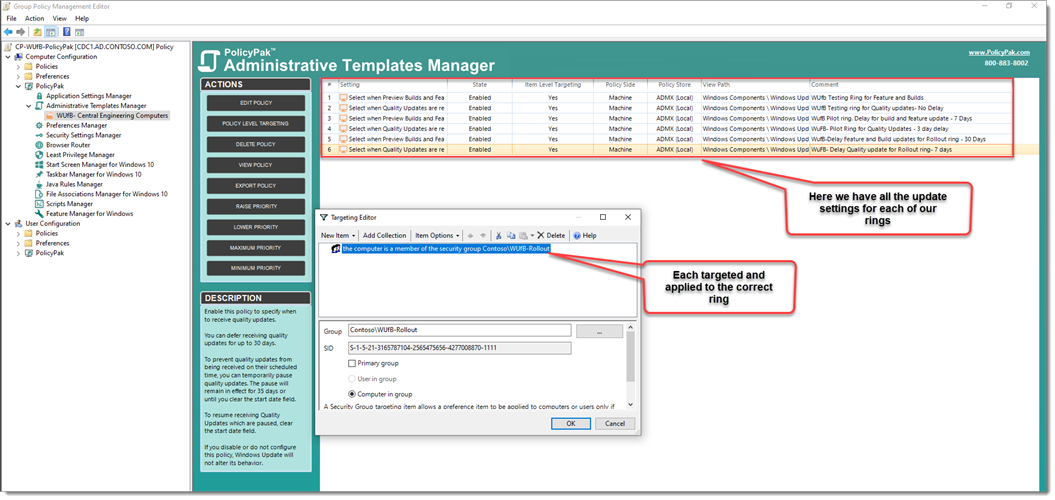
PolicyPak Admin Templates Manager uses Item Level Targeting to apply the right policies to the right rings to the right groups of computers… Easy!
We have literally compressed what were three different GPOs with 6 policy settings into one easily managed place for managing Windows Updates for Business.
And you can keep using this same GPO and repeat the process; one new collection for each computer type, then tuck the policy settings inside for each ring.
With PolicyPak Admin Templates Manager, there’s no more digging through tons of GPOs within OUs to find what and where that Windows update Group Policy setting might be.
All the settings right here in one centralized, easy-to-manage place, in one single GPO.


