Jeremy Moskowitz founded PolicyPak Software after working with hundreds of customers with the same problem they couldn’t manage their applications, browsers and operating systems using the technology they already utilized.

GPO Item Level Targeting Secrets That Will Blow Your Mind
GPO Item Level Targeting is one of the most powerful tools you can use as a Group Policy admin. First of all, You know how important it is to segregate your domain into applicable OUs for different user and computer AD accounts (see Figure 1).
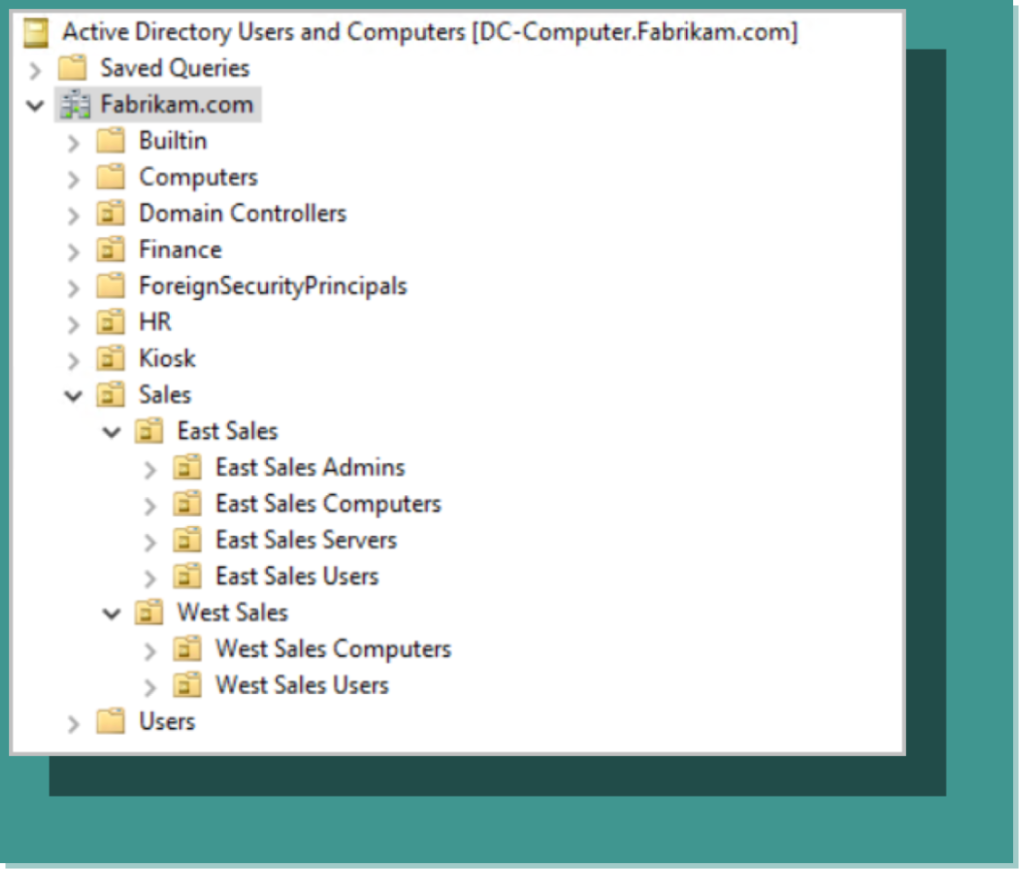
Figure 1: Example OUs for an active directory.
While this approach by itself may have been completely sufficient at one time, in today’s complicated networks you need more granular control over GPO delegation, for instance, at times when you want to apply a GPO to members of a designated security group only or when a user is on a particular IP address range.
BLOG: How to Apply Item Level Targeting
Item-Level Targeting lets you define how Group Policy settings apply to Active Directory users or computers by setting conditions. You perform the process by first selecting conditional logic statements like AND, OR, and NOT. These best practices will help you get more out of Item-level targeting.
There are few other ways you can target GPOs (or what they do) to users:
- Group membership approach
- WMI approach
- Item-Level Targeting (ILT) approach
We’ll briefly explore the first two options, and then dive into ILT and why it can help you out immensely.
GPO Item Level Targeting by Group
A basic way to target GPOs is to use security filtering so that the GPO only applies to a designated group or groups. By default, a GPO applies to all authenticated users within the container that the GPO is linked to, such as an OU. In the example in Figure 2 below, the GPO is being applied to all authenticated users within the “East Sales Users” OU.
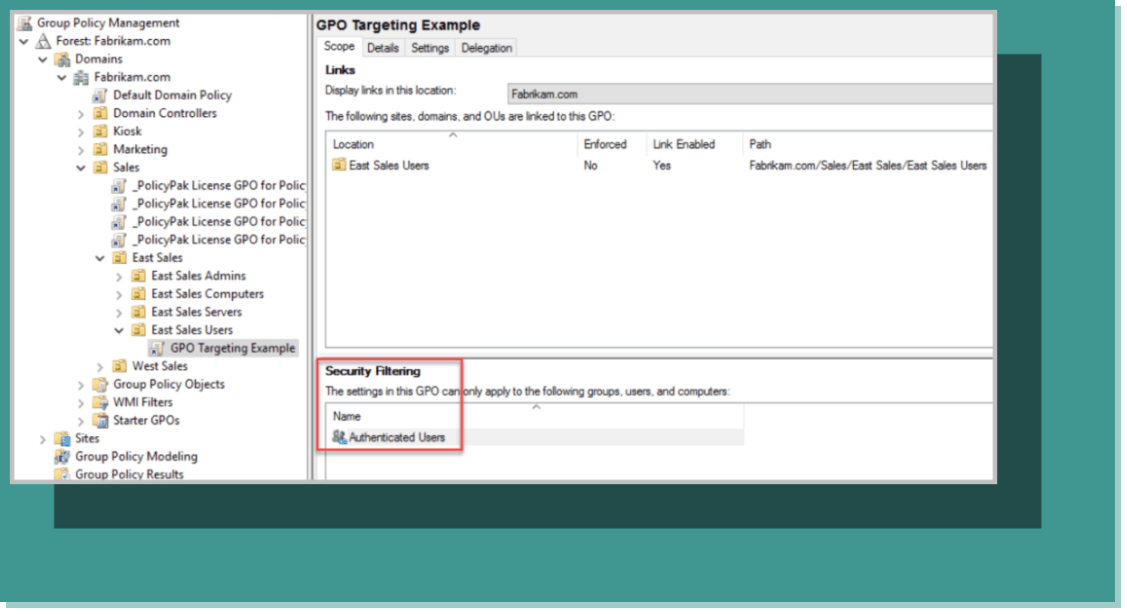
Figure 2: Applying a GPO to the OU “East Sales Users.”
Using the Security Filtering settings, you can delete the Authenticated Users group and select one or more designated groups. In Figure 3, the GPO is being targeted to the Traveling Sales Users group.
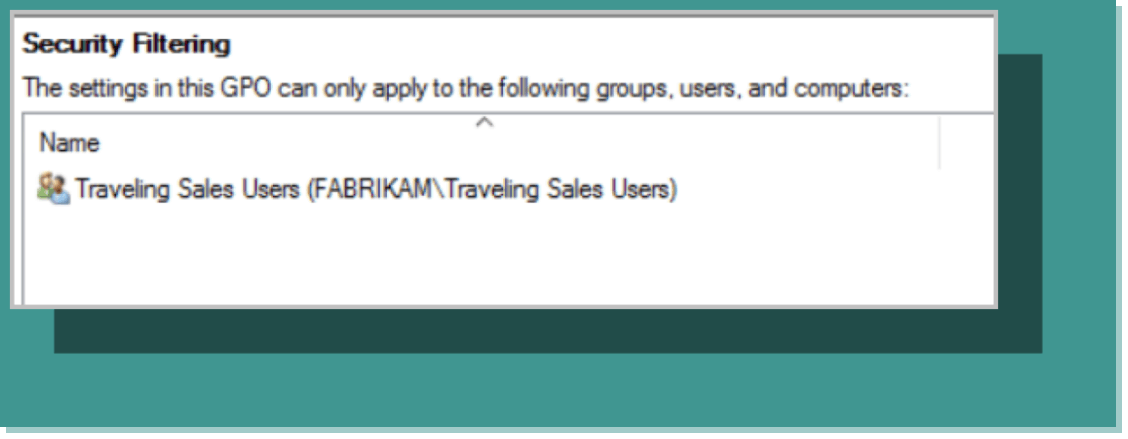
Figure 3: Using security filtering to target a specific group.
GPO Item Level Targeting by WMI
Another option for targeting GPOs is WMI filtering. This is applicable for certain circumstances such as targeting a specific operating system. If you wanted to target only machines running Windows 10, you could create the following WMI query:
select * from Win32_OperatingSystem where Version like “10.%” and ProductType=”1″
You would then create a WMI filter within Group Policy Management and a query statement, as shown in Figure 4 below.

Figure 4: Creating a WMI filter and query statement.
While WMI does do the job in some cases, it has a number of shortcomings.
- It requires accurately written query statements.
- It is used per GPO which can lead to GPO sprawl for complex environments in which you need to filter many settings with different filters.
- It is slow and can lead to long login times.
- It can be unpredictable.
For more information about whether or not to use WMI filtering, check out our article that explains WMI filtering and its downsides: https://www.policypak.com/pp-blog/group-policy-wmi-filtering-and-group-policy-preferences-item-level-targeting-everything-you-need-to-know
BLOG: WMI Filtering Tips and Tricks
Why is WMI important when it comes to Group Policy? WMI provides a way for you to filter Group Policy Objects based on the result of a WMI query. Where might this come in handy? It can help you custom target your GPOs so the right GPOs apply within just the right conditions.
GPO Item Level Targeting with Everything Else
If OU design and targeting by group are just ok and WMI is not great, what’s other choice do you have for targeting GPOs? Let’s talk about Item Level Targeting.
Item Level Targeting gives you a whole gamut of things to target such as:
- Security group
- Computer OS
- Computer name
- IP address range
- File or registry match
- Language
You also don’t need to know how to write a query statement because it is all point and click. Although it sounds good so far, there are a couple of shortcomings.
- It is only available in Group Policy Preferences.
- It is only for domain-joined computers.
In other words, if want to create a GPO using Administrative Templates or create a policy for non-domain-joined computers, you are out of luck.
Item-Level Targeting and Group Policy Preferences
Let’s work through an example of a situation where all admins can use ILT, like with a Registry Item change. Microsoft Group Policy Preferences gives you a number of granular control functions including ILT. ILT allows you to change the scope of individual preference items, so they apply only to selected users or computers.
The screenshot in Figure 5 shows a Group Policy Preferences policy that creates a registry key. Once the registry configuration is complete, you can then access its properties and click the common tab where you can select “Item-level targeting” as is shown in the screenshot below. Note that ILT is available for any GPP setting.

Figure 5: Selecting “Item-level targeting” for a Group Policy Preferences policy.
You can then select an item to target. In this case we are going to choose “Security Group,” as shown in Figure 6.
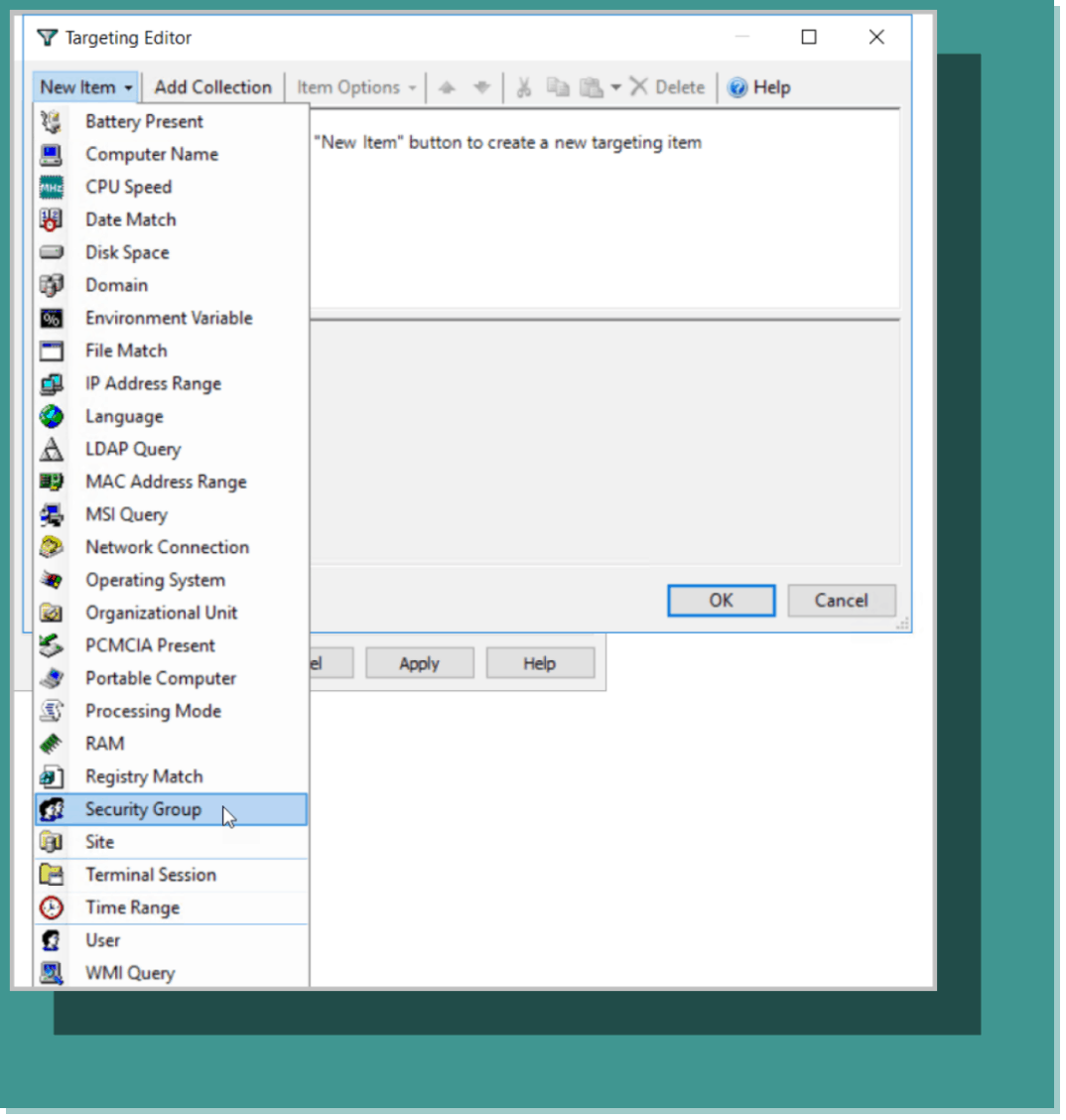
Figure 6: Targeting security groups in the Targeting Editor.
We want to start out by targeting a domain security group. In the screenshot below in Figure 7, we have chosen the Traveling Sales Users group as we did earlier.
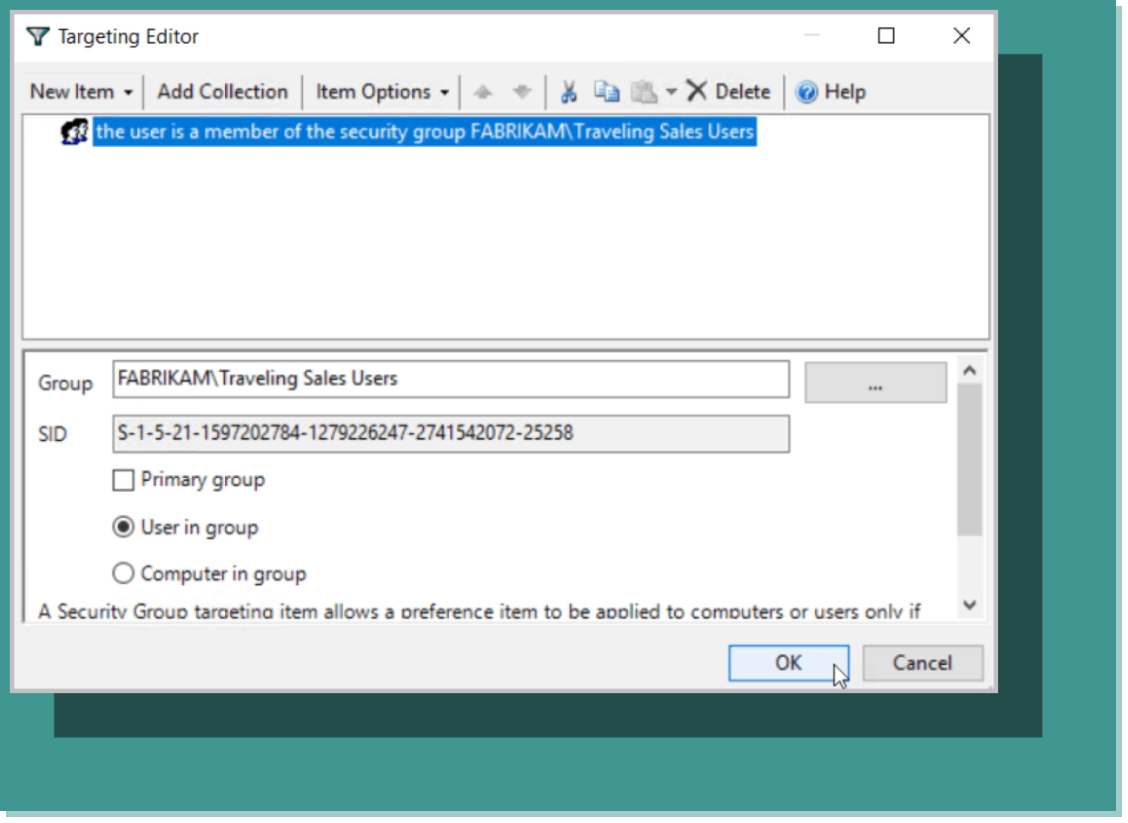
Figure 7: Targeting the Traveling Sales Users group.
Now the registry item will be updated for all group members in the linked OU as well as all nested OUs, unless blocked for inheritance.
FREE TRIAL: GPO Reduction and Transitions Pak
Reduce and consolidate Group Policy Objects and Settings for a more modernized and efficient Windows infrastructure. The PolicyPak GPO Reduction and Transitions Pak manages complex environments in a way that eliminates sprawl and simplifies administration.
While having the ability to target security groups is cool, ILT provides far more granularity. For example, what if the registry key were only applicable for machines that run Windows 10 Professional edition? In this case, you can add a condition that members of the security group must also be running that particular OS, as shown below in Figure 8. Of course, if the combined value of all targeting items for a preference item is false, then the settings in the GPPrefs item are not applied to the user or computer.

Figure 8: Restricting the application of the GPO to users with Windows 10 Professional.
Let’s dive even deeper with ILT. You can use varying logical operators (“And,” “Or,” “Is,” and “Is Not”) to delegate a GPO to members of one group or another. You can also incorporate the use of collections. In the example below in Figure 9, the GPO is assigned to members of either the Traveling Sales Users group or East Sales Managers who also meet the conditions of a collection consisting of two settings. In this case, users of either group must be logged on a portable computer and running Windows 10 Professional edition. Notice the use of logical operators as well.

Figure 9: Targeting groups using logical operators and collections.
Using PolicyPak to Overcome Limitations of GPO Item Level Targeting
All of these options make ILT seem like a good solution, but the problem is that it is not natively available for the more than 4,000 Administrative Templates settings that you use every day. In addition, there are other items in Group Policy that don’t have ILT where it would be really useful (like with 3rd party add-ons).
Is there some magical workaround for this? Actually, yes. Simply use PolicyPak.
PolicyPak is a modern desktop management solution that maximizes the management tools you already have. PolicyPak allows you to configure, deploy, and manage policies for your Windows environments using Microsoft Group Policy Editor, SCCM, or other systems management systems. Its solution suite gives you super admin powers to do things such as use ILT with Administrative Templates settings. As you can see from the screenshot below in Figure 10, the policy creation process mimics that of traditional group policy.

Figure 10: The policy creation process with PolicyPak.
PolicyPak Admin Templates Manager includes all of the same administrative templates settings you are familiar with, including third party templates you may be using as well. You can enable or disable the setting of your choice. In the example below in Figure 11, we want to prohibit access to Control Panel and PC settings.
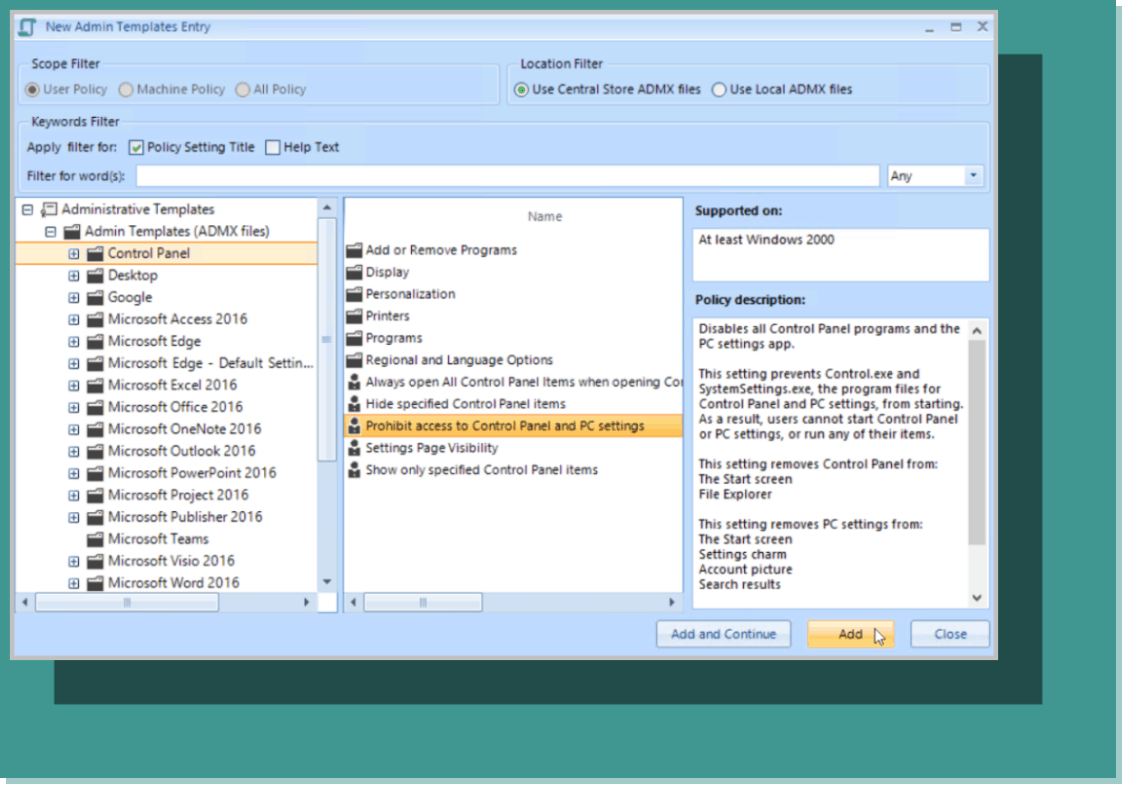
Figure 11: Creating a new Admin Templates entry.
Notice the Item Level Targeting button is available within the properties page (see Figure 12), thus giving you identical access to the ILT feature as shown below.

Figure 12: Using the Item-Level Targeting feature of PolicyPak Admin Templates Manager.
By utilizing ILT for all of your GPOs, you can consolidate your GPOs into a much smaller and more manageable number or even a single GPO. You can watch a video to see how to use PolicyPak ILT to simplify your GPO environment. You can also get more information on how PolicyPak can apply ILT to MDM-enrolled and non-domain-joined machines.
Summary
Item Level Targeting is a great feature to maximize your Group Policy Preferences environments even with its shortcomings; however, you don’t have to accept its limitations. With PolicyPak, you can meet the demands of today’s mobile and remote work strategies by deploying any traditional GPO to any Windows machine you want using ILT.


