Jeremy Moskowitz founded PolicyPak Software after working with hundreds of customers with the same problem they couldn’t manage their applications, browsers and operating systems using the technology they already utilized.
HIPAA Changes 2021: Three Ways to Secure Patient Data
HIPAA Changes for 2021 are critical for ensuring patient data is secure and protected. HIPAA is probably the most well-known cybersecurity compliance regulation in the U.S. It was originally written as a set of minimum standards for those organizations that fall under its jurisdiction. But while other major cybersecurity regulatory sets such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) have garnered continued headlines due to their dynamically changing guidelines, the HIPAA set of compliance standards has remained relatively stagnant since 2013 when the Omnibus Rule was published.
The world has certainly changed in the past seven years, however. In fact, when HIPAA was first drafted 24 years ago, legislators had no idea about the type of technologies that would transform the health industry sector in the coming decades. There is no doubt that HIPAA changes for 2021 will be coming, however, since the Department of Health and Human Services just finalized rules to provide patients more control of their health data. There is also a need for changes in reaction to the significant increase in cyberattacks on the healthcare sector.
HIPPA Changes 2021: The Result of Recent HIPAA Settlements?
While there hasn’t been a lot of news concerning HIPPA 2021 Changes, the same isn’t true for HIPAA regulators. There is currently a lot going on when it comes to HIPAA litigation. Cases have been active and ongoing with some of them resulting in large settlements:
- The U.S. Department of Health and Human Services reported a settlement just last month in which Aetna agreed to pay $1 million to the Office for Civil Rights (OCR) concerning three HIPAA data breaches that occurred in 2017.
- A settlement of $2.3 million was announced in September of 2020 between CHSPSC LLC. and OCR. The settlement involved perpetual noncompliance with the HIPAA Security Rule. Violations included the failure to conduct a risk analysis and the failure to implement security incident procedures and access controls, despite being informed of an attack by the FBI.
- Athens Orthopedic Clinic was instructed two months ago to pay $1.5 million to OCR and implement a corrective action plan after a breach in June 2016 led to an investigation into potential HIPAA violations.
HIPAA 2020 Changes: What We Saw Last Year
Earlier last year, HHS did announce some temporary changes to HIPAA. The changes were intended to give healthcare providers and partner organizations more flexibility in how they share protected health information (PHI) as a result of the pandemic. An example was the waiving of various HIPAA rules concerning telehealth providers. As long as the telehealth provider acted in good faith, personnel could use communications technology such as Zoom, FaceTime, or Skype that does not necessarily comply with HIPAA requirements. Community-based testing sites were also allowed leeway as well. These provisional changes are described in detail on the HHS website.
Healthcare providers should not think that this easing of HIPAA enforcement is the new norm. These changes are set to immediately expire once the COVID emergency is over. In the case of hospitals, announced exceptions can only occur within a 72-hour period once a disaster protocol has been implemented. This relaxation of HIPAA standards has come at a heavy price, however. Because of the shortcuts taken in some cases, ransomware attacks have doubled in the third quarter of 2020, making it one of the most active years on record. In addition, healthcare providers should not think that this easing of HIPAA enforcement is the new norm. These changes are set to immediately expire once the COVID-19 emergency is over. Today’s climate shows us that it is time to start focusing on tightening standards again.
Windows 10 and HIPAA
Although HIPAA does not reference the Windows 10 operating system, one thing is certain. Windows client machines must be running Windows 10 in order to be HIPAA compliant as Windows 7 is not. Keeping your Windows machines updated is also imperative. Ensuring that every Windows device is running Windows 10 is an important step in meeting HIPAA compliance.
Three Ways to Secure Patient Data
Below we’ll discuss three ways that you can secure your patient data, including how to make use of components from PolicyPak’s suite of products to enhance your ability to enforce encryption and application whitelisting.
Using Encryption to Secure Patient Data
When it comes to internal storage, encryption is not required by HIPAA, but it is highly encouraged. That’s because it is the best way to secure data at rest. If your organization currently uses devices running a Windows 10 enterprise operating system, then encryption is certainly an appropriate and reasonable measure because you’ve already paid for it. If your computers are domain-joined and managed by the latest Windows Server editions, then you can centrally manage BitLocker settings on those particular devices.
Protecting ePHI with PolicyPak Administrative Templates Manager
But what about computers that are not domain-joined and machines that are enrolled in an MDM other than Intune (which supports some BitLocker settings)? What about the simple protection of not writing to removable data drives? That’s where PolicyPak Admin Templates Manager comes in. PolicyPak integrates with the Group Policy Editor your team already knows how to use. It uses the same ADMX definitions you’re already using, but enables you to use them in new ways.
Let’s say you want to configure and deploy BitLocker settings to a set of designated devices. Just like Group Policy, with PolicyPak Admin Templates Manager it all starts with the creation of a new policy (see Figure 1).

Figure 1: Creating a new policy in PolicyPak Administrative Templates Manager.
PolicyPak lets you configure any of the included ADMX BitLocker settings. In the example below, we want to enable the “Enforce drive encryption type for fixed data drives” and “Deny write access to fixed drives not protected by BitLocker” settings (see Figure 2).

Figure 2: Configuring BitLocker settings with PolicyPak.
Stopping Users from Clicking on Malicious Code
HIPAA is all about reducing your organization’s risk exposure, but achieving this is challenging in an environment where users don’t show enough caution with the files they download and the links they click on. Wouldn’t it be great to create a policy that only allows users to run the executables and applications you approve of?
This is what application whitelisting (AWL) is all about. The problem with AWL is the time involved in creating the initial whitelist and updating it as your dynamic environment evolves. Instead of wasting your time, you can use PolicyPak SecureRun™. The premise behind SecureRun™ is simple. If an application wasn’t installed by an administrator or someone on the SecureRun™ Members list, it will not run. When users download files off the Internet or copy them from a USB drive, etc., they own the file, making it easy to prevent these specific files from running (see Figure 3).
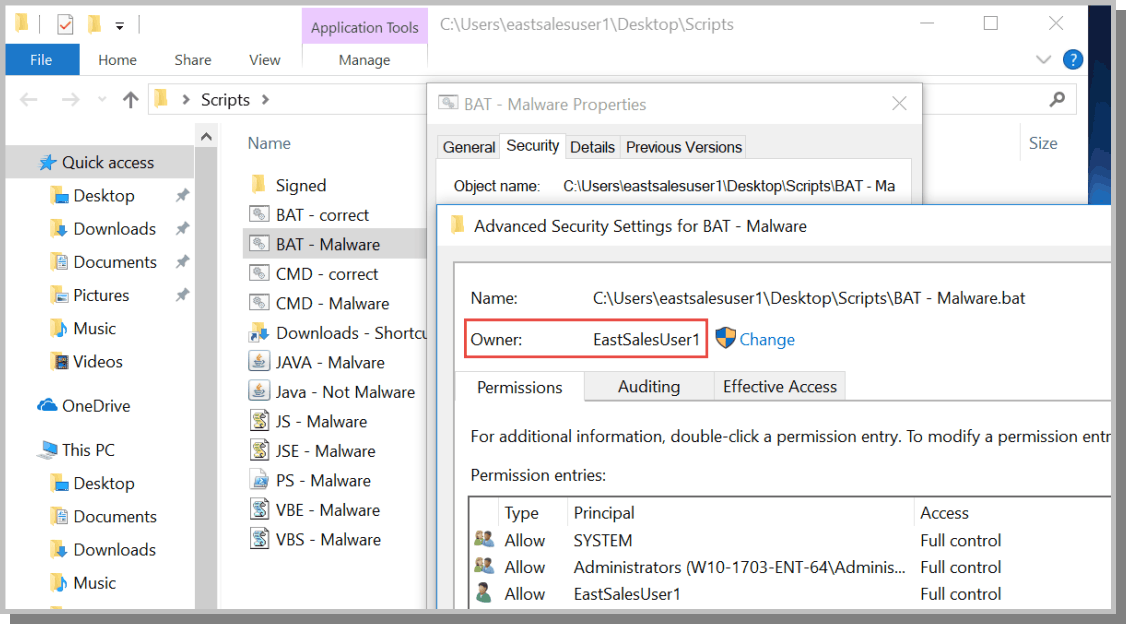
Figure 3: Users own the files they download, making it easy to prevent these files from running.
In other words, any file, script, MSI, or application that wasn’t installed, downloaded, or created by anyone on the SecureRun™ Members list, will not run. Below is the default SecureRun™ Members list (see Figure 4). You can add or delete members according to your individual security needs. Typically, the PolicyPak SecureRun™ defaults are sufficient for most organizations’ needs.

Figure 4: SecureRun™ Members list.
The final result can be seen in the screenshot below, where applications installed by the Admin are allowed, and everything else is automatically blocked (see Figure 5).

Figure 5: Applications being blocked by SecureRun™.
Summary
Cybersecurity is a moving target and compliance regulations must dynamically adapt to them in order to remain relevant. Whether your company is bound by the rules of HIPAA, CCPA, or GDPR, you can stay ahead of the curve with PolicyPak and its solution suite of products, each designed to ensure that you have complete managerial control of the user desktop environment.


